Millions Stolen: Inside The Office365 Hacking Targeting Executives
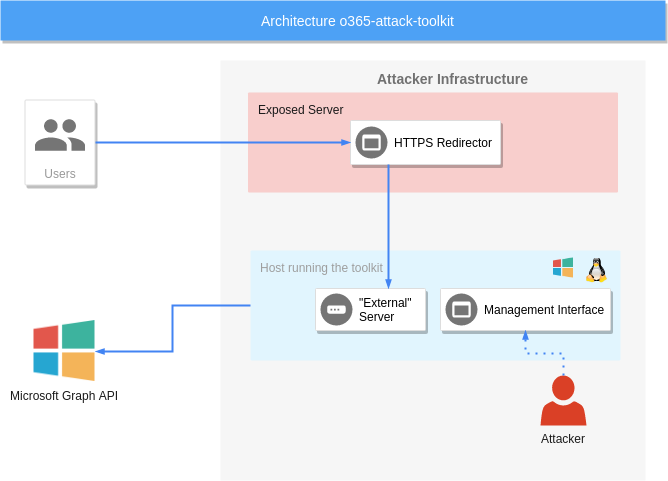
Table of Contents
The Sophistication of Modern Office365 Attacks
Modern Office365 attacks go far beyond the simple phishing emails of the past. These are highly targeted, sophisticated campaigns designed to bypass even the most robust security measures. Unlike traditional phishing scams that rely on generic lures, these attacks utilize advanced techniques to exploit vulnerabilities within Office 365's architecture and circumvent multi-factor authentication (MFA). Hackers are increasingly leveraging automation and AI to enhance their effectiveness.
- Exploitation of compromised credentials: Hackers often acquire credentials from other breaches and use them to access Office365 accounts through credential stuffing or brute-force attacks. This emphasizes the importance of strong, unique passwords and password management tools.
- Sophisticated phishing techniques: Spear phishing, a highly targeted form of phishing, is frequently employed. These attacks use personalized information to make the emails seem legitimate, increasing the chances of success. CEO fraud, where hackers impersonate senior executives to trick employees into transferring funds, is also a significant threat.
- Vulnerabilities in third-party apps: Many organizations integrate third-party apps with Office365, creating potential entry points for hackers. Compromising a less secure third-party app can provide access to the entire Office365 environment.
- Social engineering: Manipulating individuals to reveal sensitive information or perform actions that compromise security remains a highly effective tactic. Social engineering often precedes technical exploits, weakening defenses before the attack begins.
Common Tactics Used in Office365 Executive Hacks
Executives are prime targets due to their access to sensitive financial information and their influence within the organization. A successful attack against an executive can have devastating consequences. Hackers use various methods to target these high-value individuals:
- Credential stuffing and brute-force attacks: These automated attacks attempt to use stolen credentials or guess passwords to gain access to accounts. Strong, unique passwords and MFA are critical defenses against these attacks.
- Exploiting weak passwords and password reuse: Executives, like all users, are vulnerable to weak passwords and the practice of reusing passwords across multiple accounts. This single point of failure can compromise access to numerous sensitive systems.
- Targeting personal devices and accounts: Hackers may target personal devices or accounts connected to an executive's professional accounts, using these as entry points into the organization's systems.
- Compromised vendor accounts: Attackers may target vendors with access to the organization's Office365 environment, gaining access indirectly through a compromised third-party account.
- Impact of successful attacks: The consequences of a successful Office365 executive hack can be severe, including significant financial losses, data breaches leading to regulatory fines, irreparable reputational damage, and costly legal ramifications.
Recognizing the Warning Signs of an Office365 Compromise
Early detection is crucial in mitigating the damage from an Office365 compromise. Organizations should be vigilant in monitoring for subtle signs of an attack, including both technical and behavioral indicators:
- Unusual login activity: Login attempts from unfamiliar locations or devices should trigger alerts. Monitoring login activity is a fundamental security practice.
- Suspicious email activity: Unusual forwarding of emails, emails sent to unexpected recipients, or a sudden increase in email volume should raise red flags.
- Changes to user permissions or account settings: Unauthorized changes to user permissions or account settings can indicate malicious activity.
- Unexplained financial transactions: Any unusual or unexplained financial transactions should be immediately investigated.
- Unusual data access patterns: Monitoring data access patterns can help identify unauthorized access or data exfiltration attempts.
- Employee reports: Encourage employees to report any suspicious emails or activities they encounter. A strong security culture is essential for early threat detection.
Protecting Your Organization from Office365 Executive Hacks
A multi-layered security approach is vital to protect against Office365 executive hacks. Organizations should implement the following measures:
- Robust multi-factor authentication (MFA): MFA adds an extra layer of security, significantly reducing the risk of unauthorized access, even with compromised credentials.
- Strong password policies and password managers: Enforce strong password policies and encourage the use of password managers to help users create and manage complex, unique passwords.
- Security awareness training: Regular security awareness training for all employees, especially executives, is critical to educate them about phishing techniques and other social engineering tactics.
- Advanced threat protection (ATP): Implementing ATP solutions within Office365 provides advanced threat detection and protection against sophisticated attacks.
- Regular security audits and penetration testing: Regular security audits and penetration testing help identify vulnerabilities and weaknesses in your security posture.
- Data loss prevention (DLP) measures: DLP measures help prevent sensitive data from leaving your organization's control.
- Cybersecurity incident response planning: Develop a comprehensive incident response plan to effectively manage and mitigate the impact of a successful attack.
Conclusion
The threat of Office365 hacking targeting executives is real and devastating. Millions of dollars are stolen annually, causing irreparable damage to organizations. By understanding the tactics used and implementing robust security measures, businesses can significantly reduce their risk. Don't wait until it's too late. Take proactive steps today to protect your organization from the devastating consequences of Office365 hacking. Invest in comprehensive security solutions and educate your employees to safeguard your valuable assets and reputation. Learn more about strengthening your Office 365 security and protecting your executives from targeted attacks.

Featured Posts
-
 Judge Rules Against Section 230 Protection For Banned Chemicals On E Bay
Apr 22, 2025
Judge Rules Against Section 230 Protection For Banned Chemicals On E Bay
Apr 22, 2025 -
 Stock Market Update Dow Futures Decline Dollar Falls On Trade Worries
Apr 22, 2025
Stock Market Update Dow Futures Decline Dollar Falls On Trade Worries
Apr 22, 2025 -
 Blue Origin Rocket Launch Aborted Subsystem Problem Delays Mission
Apr 22, 2025
Blue Origin Rocket Launch Aborted Subsystem Problem Delays Mission
Apr 22, 2025 -
 Navigating The Chinese Market The Struggles Of Bmw Porsche And Competitors
Apr 22, 2025
Navigating The Chinese Market The Struggles Of Bmw Porsche And Competitors
Apr 22, 2025 -
 Us South Sudan Agreement On The Return Of Deportees
Apr 22, 2025
Us South Sudan Agreement On The Return Of Deportees
Apr 22, 2025
