Inside Job? Millions Stolen Via Compromised Office365 Executive Accounts
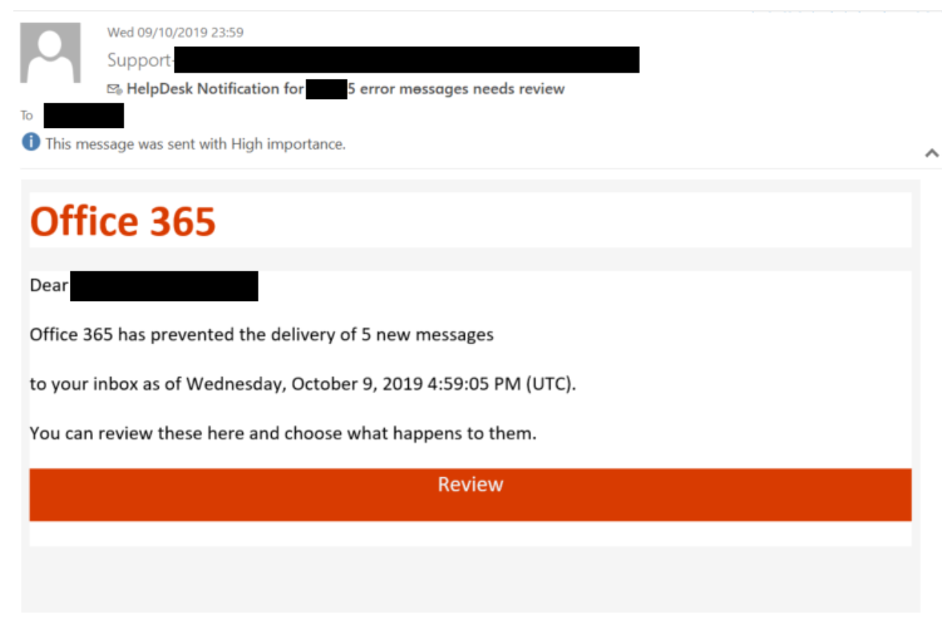
Table of Contents
How Hackers Target Executive Office365 Accounts
Cybercriminals employ increasingly sophisticated tactics to gain access to high-value Office365 executive accounts. These aren't random attacks; they're carefully planned and executed operations designed to maximize financial gain.
Phishing and Spear Phishing Attacks
Phishing and spear phishing attacks remain a highly effective method for gaining initial access. These attacks leverage social engineering, manipulating recipients into divulging sensitive information or clicking malicious links.
- Examples: Emails impersonating board members requesting urgent wire transfers, fake invoices from trusted vendors, or messages containing links to seemingly legitimate websites.
- CEO Fraud: A particularly insidious form involves impersonating the CEO or another high-ranking executive to authorize fraudulent transactions.
- Impersonation Tactics: Hackers often meticulously craft emails mimicking the writing style and communication patterns of the targeted executive to increase their chances of success. The perceived authority of the executive makes these attacks particularly effective.
Credential Stuffing and Brute-Force Attacks
Hackers also employ automated attacks to gain access to Office365 accounts.
- Weak Passwords & Password Reuse: Weak or reused passwords are easily cracked, providing hackers with access to multiple accounts across various platforms.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA significantly weakens security, allowing hackers to easily bypass password protection.
- Data Breaches: Data breaches on other platforms often result in a trove of stolen credentials, which are then used in credential stuffing attacks against Office365 accounts. This makes it crucial to monitor for breaches affecting other accounts your executives may use.
Exploiting Software Vulnerabilities
Zero-day exploits and other software vulnerabilities can be exploited to bypass security measures and gain unauthorized access to Office365 accounts.
- Regular Software Updates: Regular updates are crucial for patching known vulnerabilities and minimizing the risk of exploitation.
- Vulnerability Scanning & Penetration Testing: Proactive security measures such as vulnerability scanning and penetration testing identify and address potential weaknesses before they can be exploited.
- Unpatched Software: Outdated software creates significant vulnerabilities, acting as an open door for hackers.
The Devastating Financial Impact of Office365 Executive Account Breaches
The financial consequences of compromised Office365 executive accounts can be catastrophic. The scale of losses can run into millions, causing long-term damage to the organization.
Financial Losses from Fraudulent Transfers
Successful attacks often lead to significant financial losses.
- Wire Transfers: Hackers can initiate fraudulent wire transfers, siphoning funds directly from the company's accounts.
- Fraudulent Invoices: Compromised accounts can be used to authorize fraudulent invoices, leading to substantial financial losses.
- Payroll Manipulation: Hackers can manipulate payroll systems, diverting funds to their own accounts. This often goes unnoticed until much later. Examples of real-world incidents involving millions of dollars stolen through these methods are readily available in cybersecurity news.
Reputational Damage and Loss of Investor Confidence
Beyond direct financial losses, compromised accounts inflict significant reputational damage.
- Stock Price Drops: News of a security breach can lead to a dramatic drop in the company's stock price.
- Loss of Clients: Damaged trust can result in the loss of clients and business opportunities.
- Damage to Brand Image: A security breach can severely damage the company's brand image and reputation, potentially impacting long-term sustainability. This impacts all stakeholders – employees, investors, and customers.
Legal and Regulatory Penalties
Organizations facing Office365 executive account compromises face potentially hefty legal and regulatory penalties.
- GDPR Compliance: Failure to comply with data protection regulations like GDPR can result in substantial fines.
- SEC Regulations: Publicly traded companies are subject to SEC regulations, which impose stringent requirements for data security.
- Potential Lawsuits: Compromised accounts can lead to lawsuits from affected individuals and organizations. The costs associated with legal battles and investigations can be immense.
Protecting Your Office365 Executive Accounts: Best Practices
Protecting your organization from Office365 executive account compromises requires a multi-layered approach combining technology and employee training.
Implementing Robust Multi-Factor Authentication (MFA)
MFA is crucial in preventing unauthorized access.
- Authenticator Apps: Using authenticator apps on smartphones adds an extra layer of security.
- Hardware Tokens: Hardware tokens provide a highly secure form of MFA.
- Extra Layer of Security: MFA significantly reduces the risk of successful attacks, even if credentials are compromised.
Employee Security Awareness Training
Educating employees about phishing and other social engineering tactics is critical.
- Regular Phishing Simulations: Regular phishing simulations help employees identify and report suspicious emails.
- Awareness Campaigns: Regular awareness campaigns reinforce best practices and highlight current threats.
- Email Security Best Practices: Training on best practices for email security, including identifying phishing attempts, is essential.
Regular Security Audits and Penetration Testing
Proactive security measures are essential for identifying and addressing vulnerabilities.
- Regular Security Assessments: Regular security assessments help identify potential weaknesses in your security posture.
- Vulnerability Scanning: Regular vulnerability scans detect and report potential security flaws.
- Penetration Testing: Penetration testing simulates real-world attacks to identify and address vulnerabilities. Employing professional cybersecurity experts is highly recommended.
Conclusion: Securing Your Organization Against Office365 Executive Account Compromises
The threat of Office365 executive account compromises is real and significant, leading to devastating financial losses and reputational damage. By implementing robust security measures such as MFA, comprehensive employee training, and regular security audits, organizations can significantly reduce their vulnerability. Don't become the next victim of Office365 executive account compromises. Implement robust security measures today to protect your organization and its valuable assets. [Link to relevant cybersecurity resources]

Featured Posts
-
 Parker Mc Collums Bold Claim Hes Coming For George Straits Crown
May 14, 2025
Parker Mc Collums Bold Claim Hes Coming For George Straits Crown
May 14, 2025 -
 Naturschutz In Der Saechsischen Schweiz 190 000 Baeume Gepflanzt
May 14, 2025
Naturschutz In Der Saechsischen Schweiz 190 000 Baeume Gepflanzt
May 14, 2025 -
 Pre Ipo Challenges A Forerunners Guide To Alternative Strategies
May 14, 2025
Pre Ipo Challenges A Forerunners Guide To Alternative Strategies
May 14, 2025 -
 Bellingham Brother Could Join Manchester United
May 14, 2025
Bellingham Brother Could Join Manchester United
May 14, 2025 -
 El Legado De Joaquin Caparros En El Sevilla Fc 25 Anos De Presentaciones Y Exitos
May 14, 2025
El Legado De Joaquin Caparros En El Sevilla Fc 25 Anos De Presentaciones Y Exitos
May 14, 2025
Latest Posts
-
 500 Evra Za Patike Da Li Vredi Investitsi A U Modele Novaka Okovi A
May 14, 2025
500 Evra Za Patike Da Li Vredi Investitsi A U Modele Novaka Okovi A
May 14, 2025 -
 Escape To Chocolate Bliss Lindt Opens Its Flagship London Store
May 14, 2025
Escape To Chocolate Bliss Lindt Opens Its Flagship London Store
May 14, 2025 -
 Novakove Patike Pregled Modela Od 1 500 Evra I Vishe
May 14, 2025
Novakove Patike Pregled Modela Od 1 500 Evra I Vishe
May 14, 2025 -
 Lindt Unveils Stunning Central London Chocolate Store
May 14, 2025
Lindt Unveils Stunning Central London Chocolate Store
May 14, 2025 -
 Patike Novaka Okovi A Tsena Od 1 500 Evra I Njikhove Karakteristike
May 14, 2025
Patike Novaka Okovi A Tsena Od 1 500 Evra I Njikhove Karakteristike
May 14, 2025
