Hacker Accused Of Millions In Office365 Executive Account Breaches

Table of Contents
The Scale of the Office365 Breach and Financial Losses
The recent Office365 executive account breach resulted in staggering financial losses, reportedly exceeding [Insert reported or estimated amount] in stolen funds and associated costs. While the exact number of compromised executive accounts remains undisclosed, the impact is far-reaching. The potential long-term consequences for the affected companies include significant financial repercussions and lasting reputational damage.
- Specific examples of financial damage: The breach led to fraudulent wire transfers of substantial sums, the theft of sensitive intellectual property, and the exposure of confidential business data, potentially impacting future deals and investor confidence.
- Cost of remediation and incident response: The cost of investigating the breach, containing the damage, notifying affected parties, and implementing enhanced security measures will add significantly to the overall financial burden.
- Reputational damage: The negative publicity surrounding the breach can severely damage a company's reputation, impacting customer trust, investor confidence, and future business opportunities. This damage can extend far beyond the immediate financial losses.
Methods Used by the Hacker in the Office365 Executive Account Breach
The sophistication of the attack targeting these executive accounts is evident. The hacker likely employed a combination of techniques to gain access, including advanced phishing campaigns, credential stuffing, and possibly exploiting previously unknown vulnerabilities (zero-day exploits). Their focus on high-level executives suggests a targeted approach, emphasizing the need for tailored security protocols.
- Specific examples of phishing techniques: The attackers likely utilized highly personalized spear-phishing emails or even "whaling" attacks, specifically designed to trick executives into revealing their credentials or clicking malicious links.
- Exploited zero-day vulnerabilities: While not confirmed, the possibility of exploiting unknown vulnerabilities in Office365 or related applications cannot be ruled out, highlighting the need for constant software updates and security patching.
- Analysis of the hacker's tools and infrastructure: The investigation into the breach is likely revealing insights into the hacker's tools, techniques, and procedures (TTPs), allowing cybersecurity firms to develop better defenses against similar future attacks.
Impact on Businesses and the Importance of Office365 Security
This type of breach goes far beyond simple financial losses; it erodes business trust, disrupts operations, and creates significant legal and regulatory challenges. The loss of sensitive data, including customer information and intellectual property, can lead to substantial fines and legal action.
- Consequences of data breaches: Companies face hefty fines under regulations such as GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act), along with potential lawsuits from affected customers and partners.
- The role of compliance regulations: Meeting compliance requirements is crucial not only to avoid penalties but also to maintain customer trust and a positive public image.
- Importance of employee training and awareness: Regular security awareness training for employees is paramount to minimizing the risk of successful phishing attacks and other social engineering attempts. Empowered employees are the first line of defense.
Best Practices for Securing Office365 Accounts Against Future Breaches
Protecting your Office365 environment requires a multi-layered approach. Implementing strong security measures is essential to prevent future breaches.
- Multi-Factor Authentication (MFA): Implement MFA immediately. This adds an extra layer of security, requiring more than just a password to access accounts.
- Advanced Threat Protection (ATP): Utilize Office 365 ATP to detect and prevent malicious emails, phishing attempts, and other advanced threats.
- Regular security audits and penetration testing: Conduct regular security assessments to identify vulnerabilities and ensure your security measures are effective. Penetration testing simulates real-world attacks to uncover weaknesses.
- Strong password policies: Enforce strong password policies, requiring complex passwords and regular changes, and consider using a password manager.
Don't underestimate the importance of keeping software updated and patching vulnerabilities promptly. Regular training and awareness programs for your employees are also vital.
Conclusion
The devastating impact of this Office365 executive account breach highlights the critical need for proactive cybersecurity strategies. The financial and reputational risks are substantial, emphasizing the importance of robust security measures. The methods employed by the hacker underscore the sophistication of modern cyber threats and the necessity of a multi-layered security approach. Don't become the next victim of an Office365 breach. Implement robust security measures today to protect your organization's valuable data and reputation. Learn more about securing your Office365 environment by [link to relevant resource].

Featured Posts
-
 Human Centered Ai A Conversation With Microsofts Design Lead
Apr 26, 2025
Human Centered Ai A Conversation With Microsofts Design Lead
Apr 26, 2025 -
 Nato Expansion And Ukraine Understanding Trumps Opposition
Apr 26, 2025
Nato Expansion And Ukraine Understanding Trumps Opposition
Apr 26, 2025 -
 Harvards Challenges A Conservative Professor Offers Solutions
Apr 26, 2025
Harvards Challenges A Conservative Professor Offers Solutions
Apr 26, 2025 -
 Cassidy Hutchinson Key Witness To Reveal All In Upcoming Memoir
Apr 26, 2025
Cassidy Hutchinson Key Witness To Reveal All In Upcoming Memoir
Apr 26, 2025 -
 Building Voice Assistants Made Easy Open Ais 2024 Announcements
Apr 26, 2025
Building Voice Assistants Made Easy Open Ais 2024 Announcements
Apr 26, 2025
Latest Posts
-
 Analysis Teslas Price Adjustments And Pre Tariff Inventory In Canada
Apr 27, 2025
Analysis Teslas Price Adjustments And Pre Tariff Inventory In Canada
Apr 27, 2025 -
 Understanding Teslas Canadian Price Increase And Inventory Strategy
Apr 27, 2025
Understanding Teslas Canadian Price Increase And Inventory Strategy
Apr 27, 2025 -
 Teslas Canadian Price Hike A Strategic Move To Clear Pre Tariff Stock
Apr 27, 2025
Teslas Canadian Price Hike A Strategic Move To Clear Pre Tariff Stock
Apr 27, 2025 -
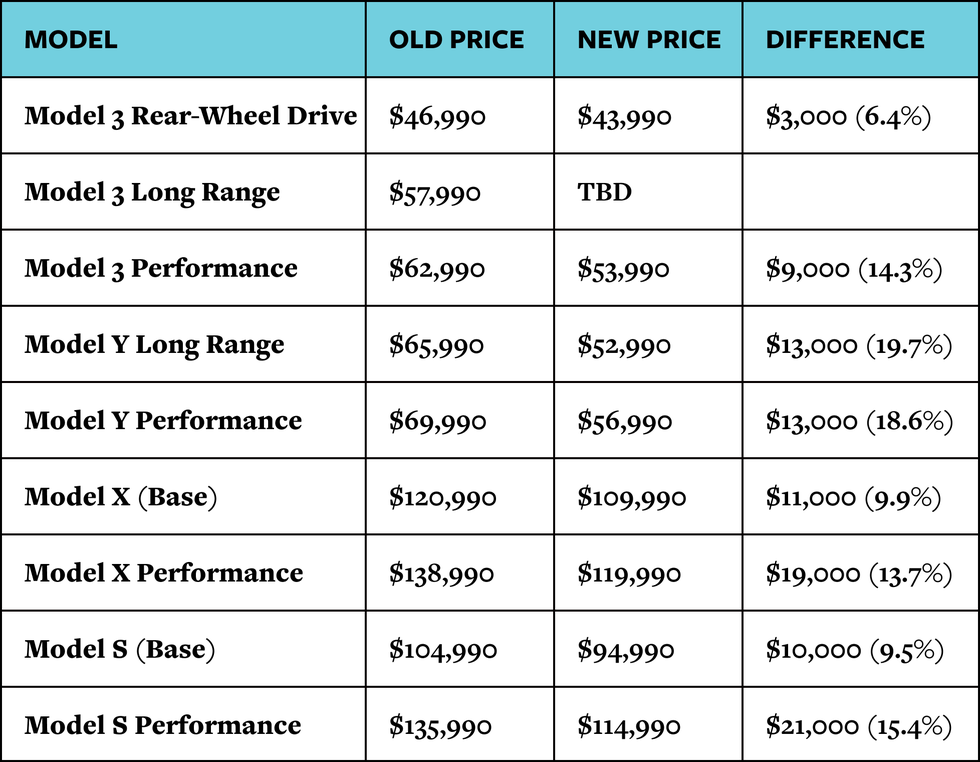 Tesla Canada Price Increase Pre Tariff Inventory Push Explained
Apr 27, 2025
Tesla Canada Price Increase Pre Tariff Inventory Push Explained
Apr 27, 2025 -
 440 Million Deal Cma Cgm Acquires Major Turkish Logistics Company
Apr 27, 2025
440 Million Deal Cma Cgm Acquires Major Turkish Logistics Company
Apr 27, 2025
