Exec Office365 Breaches Net Millions For Crook, FBI Reveals

Table of Contents
The Methods Behind Office365 Breaches
Cybercriminals employ increasingly sophisticated tactics to compromise Office365 accounts, often targeting executives who hold significant access privileges.
Phishing and Social Engineering
Sophisticated phishing campaigns are at the heart of many Office365 breaches. These attacks go beyond generic spam emails; they utilize personalized information to build trust and exploit social engineering principles.
- Examples of successful phishing attacks: Emails mimicking legitimate communications from internal colleagues or trusted vendors, containing malicious links or attachments.
- The role of spear phishing: Highly targeted attacks focusing on specific individuals within an organization, using detailed knowledge of their work and relationships.
- The use of deceptive websites: Phishing emails often lead to fake login pages designed to steal credentials. These sites mimic the legitimate Office365 login screen, making them difficult to distinguish. Keyword variations: Office 365 phishing, executive phishing, spear phishing attacks
Exploiting Vulnerabilities
Hackers actively seek and exploit known vulnerabilities in Office365 applications and systems. Outdated software, weak passwords, and unpatched systems present easy entry points.
- Common vulnerabilities: Software bugs, unpatched security flaws in applications like Outlook or SharePoint, and vulnerabilities in the underlying infrastructure.
- Outdated software: Failing to update software leaves systems exposed to known vulnerabilities with readily available exploits.
- Weak passwords: Simple or easily guessable passwords are easily cracked through brute-force attacks or readily available password lists. Keyword variations: Office365 security vulnerabilities, Microsoft 365 vulnerabilities, software vulnerabilities
Credential Stuffing and Brute-Force Attacks
Criminals often use stolen credentials from other data breaches (credential stuffing) or employ automated tools to try various password combinations (brute-force attacks).
- Data breaches leading to credential stuffing: Stolen usernames and passwords from unrelated data breaches are frequently used to attempt access to Office365 accounts.
- Techniques used in brute-force attacks: Automated scripts testing countless password combinations until a successful login is achieved.
- Password management best practices: Implementing strong, unique passwords for each account, using a password manager, and enabling multi-factor authentication. Keyword variations: Credential stuffing attacks, brute force attacks, password security
The Devastating Impact of Office365 Breaches
The consequences of a successful Office365 breach can be far-reaching and devastating, extending beyond simple data loss.
Financial Losses
The financial impact of Office365 data breaches can be catastrophic.
- Examples of large-scale financial losses: Millions of dollars lost due to ransomware attacks, data theft, and the costs of recovery and legal action.
- Costs associated with data recovery: Recovering stolen data, restoring systems, and investigating the breach are expensive and time-consuming.
- Reputational damage: The financial cost extends beyond immediate losses and includes long-term reputational damage. Keyword variations: Office365 data breaches cost, ransomware attacks, financial impact of cyberattacks
Reputational Damage
A successful breach significantly erodes trust and damages brand reputation.
- Loss of customer confidence: Customers are hesitant to work with companies that have experienced data breaches, potentially leading to lost business.
- Negative media coverage: Data breaches often receive significant media attention, harming the company's image and public perception.
- Impact on investor relations: Investors may lose confidence, leading to decreased stock value and difficulty securing funding. Keyword variations: Brand reputation damage, cyberattack reputation, trust in businesses
Legal and Regulatory Compliance Issues
Breaches often trigger legal and regulatory consequences, leading to significant fines and penalties.
- GDPR, CCPA, other relevant regulations: Failure to comply with data protection regulations like GDPR and CCPA can result in substantial fines.
- Legal actions against breached companies: Victims of data breaches may pursue legal action, leading to further financial losses and reputational damage.
- Insurance implications: Data breach insurance may not fully cover all costs associated with a breach. Keyword variations: GDPR compliance, data breach regulations, legal ramifications of cyberattacks
Protecting Your Organization from Office365 Breaches
Proactive security measures are crucial to mitigating the risk of Office365 breaches.
Implementing Strong Security Measures
Implementing strong security measures is paramount.
- Specific steps for implementing MFA: Enable multi-factor authentication (MFA) for all user accounts, requiring verification beyond just a password.
- Password managers: Encourage the use of strong, unique passwords for each account using a robust password manager.
- Security awareness training programs: Educate employees about phishing attempts, social engineering tactics, and safe password practices.
- Regular security audits: Conduct regular security audits to identify vulnerabilities and ensure compliance. Keyword variations: Office365 security best practices, multi-factor authentication (MFA), security awareness training, cybersecurity solutions
Utilizing Advanced Threat Protection
Advanced threat protection tools offer an essential layer of security.
- Examples of advanced threat protection solutions: Microsoft Defender for Office 365, other third-party solutions.
- Benefits of using these tools: Real-time threat detection, advanced malware protection, and automated response capabilities.
- Cost-benefit analysis: While these solutions have costs, the cost of a breach far outweighs the investment in protection. Keyword variations: Advanced threat protection Office365, Microsoft 365 security features, cybersecurity tools
Incident Response Planning
Having a well-defined incident response plan is crucial.
- Steps to take in case of a breach: Establish clear procedures for identifying, containing, and recovering from a security incident.
- Communication protocols: Define communication protocols for notifying stakeholders, including employees, customers, and regulatory bodies.
- Data recovery procedures: Develop comprehensive data recovery procedures to minimize data loss and ensure business continuity. Keyword variations: Incident response plan, data breach response, cybersecurity incident response
Conclusion
The FBI's findings underscore the severe and costly nature of Office365 breaches. Criminals employ a range of sophisticated methods, from phishing campaigns to exploiting software vulnerabilities, to gain unauthorized access and inflict significant damage. The consequences – financial losses, reputational damage, and legal ramifications – can be devastating for any organization. Don't become the next victim of an Office365 breach. Take control of your security today by implementing multi-factor authentication (MFA), conducting regular security audits, investing in advanced threat protection solutions, and implementing a comprehensive incident response plan. Proactive security measures are the only way to effectively mitigate the risk of costly and damaging Office365 breaches and protect your organization's valuable data and reputation.

Featured Posts
-
 Shotgun Cop Man Platforming Action Meets Devilish Challenges
May 06, 2025
Shotgun Cop Man Platforming Action Meets Devilish Challenges
May 06, 2025 -
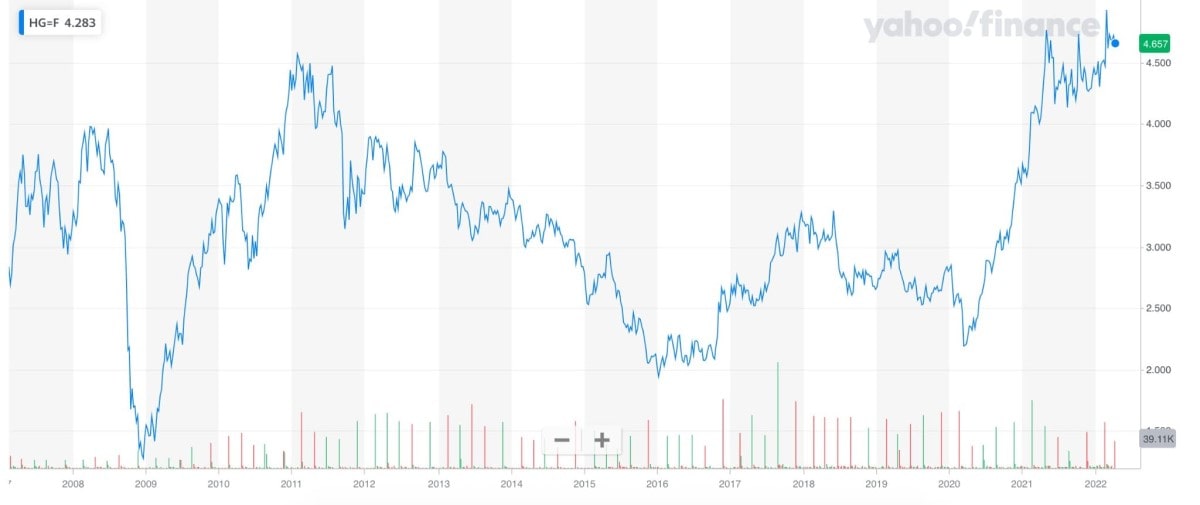 Analysis Copper Price Hike Linked To China Us Trade
May 06, 2025
Analysis Copper Price Hike Linked To China Us Trade
May 06, 2025 -
 The Superman Race Patrick Schwarzeneggers Near Miss
May 06, 2025
The Superman Race Patrick Schwarzeneggers Near Miss
May 06, 2025 -
 Mindy Kaling Quebra O Silencio Anos De Idas E Vindas Com Ex De The Office
May 06, 2025
Mindy Kaling Quebra O Silencio Anos De Idas E Vindas Com Ex De The Office
May 06, 2025 -
 Wildfire Betting A Disturbing Reflection Of Our Times
May 06, 2025
Wildfire Betting A Disturbing Reflection Of Our Times
May 06, 2025
Latest Posts
-
 Ddgs Dont Take My Son A Deeper Look At The Halle Bailey Diss Track
May 06, 2025
Ddgs Dont Take My Son A Deeper Look At The Halle Bailey Diss Track
May 06, 2025 -
 The Dont Take My Son Diss Track Ddg Vs Halle Bailey
May 06, 2025
The Dont Take My Son Diss Track Ddg Vs Halle Bailey
May 06, 2025 -
 Ddgs Dont Take My Son Diss Track Sparks Controversy Aimed At Halle Bailey
May 06, 2025
Ddgs Dont Take My Son Diss Track Sparks Controversy Aimed At Halle Bailey
May 06, 2025 -
 Ddgs New Diss Track Targets Halle Bailey Dont Take My Son
May 06, 2025
Ddgs New Diss Track Targets Halle Bailey Dont Take My Son
May 06, 2025 -
 Leon Thomas And Halle Baileys Rather Be Alone Behind The Scenes And Inspiration
May 06, 2025
Leon Thomas And Halle Baileys Rather Be Alone Behind The Scenes And Inspiration
May 06, 2025
