T-Mobile To Pay $16 Million For Data Breaches Spanning Three Years
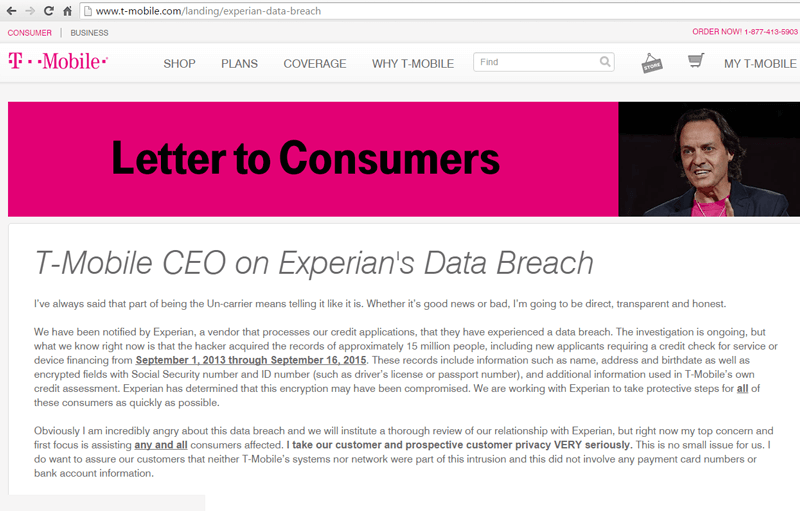
Table of Contents
Details of the T-Mobile Data Breaches
The T-Mobile data breaches unfolded over several years, exposing sensitive customer information. While the exact timeframe isn't publicly available in complete detail for all breaches, reports indicate a significant period of vulnerability. The compromised data included a range of personal information, potentially encompassing customer names, addresses, social security numbers, driver's license numbers, and financial details.
The breaches resulted from a combination of factors, including cybersecurity vulnerabilities and data security failures within T-Mobile's network. Investigations pointed to issues such as:
- Hacking Attempts: Successful attacks exploiting weaknesses in T-Mobile's systems.
- Insider Threats: Potential vulnerabilities related to internal access and employee negligence.
- System Vulnerabilities: Unpatched software and outdated security protocols that allowed unauthorized access.
Specific details on the number of customers affected by each individual breach remain partially undisclosed but the overall impact was significant. Regulatory bodies such as the Federal Communications Commission (FCC) and the Federal Trade Commission (FTC) were involved in investigations leading up to the settlement. These agencies played a vital role in assessing the extent of the data breaches and holding T-Mobile accountable.
The $16 Million Settlement
The $16 million settlement represents a significant financial penalty for T-Mobile, designed to address the consequences of their data security failures. The terms of the settlement likely involve:
- Restitution to Affected Customers: Compensation for individuals whose data was compromised.
- Investment in Data Security Improvements: Funding for enhanced security infrastructure and employee training.
- Regulatory Compliance: Measures to ensure future adherence to data protection regulations.
Beyond the monetary penalty, T-Mobile faced increased regulatory scrutiny, leading to changes in their corporate policies and procedures related to data security and network protection. This incident serves as a stark reminder of the severe financial penalties associated with data breach settlements and regulatory fines.
Lessons Learned and Future Implications
The T-Mobile data breach carries significant implications for the telecommunications industry and beyond. It underscores the crucial need for proactive cybersecurity measures, including:
- Robust Security Infrastructure: Investing in cutting-edge technology and regularly updating security systems to mitigate risks.
- Comprehensive Employee Training: Educating employees on data security best practices to minimize the risk of insider threats.
- Regular Security Audits: Conducting frequent audits to identify and address vulnerabilities before they can be exploited.
- Incident Response Planning: Developing detailed plans for handling data breaches to minimize damage and facilitate quick responses.
Transparency and timely customer notification are also paramount. When data breaches occur, companies must promptly inform affected customers, providing clear guidance on steps they can take to protect themselves. Best practices for data protection in the telecommunications sector include:
- Data Encryption: Protecting sensitive data through strong encryption methods.
- Access Control: Implementing strict access controls to limit who can access sensitive data.
- Multi-Factor Authentication: Utilizing multi-factor authentication to enhance security.
- Data Loss Prevention (DLP): Implementing DLP tools to prevent sensitive data from leaving the organization's control.
Conclusion
The T-Mobile data breach and the subsequent $16 million settlement highlight the significant financial and reputational consequences of inadequate cybersecurity measures. The incident serves as a powerful reminder of the critical importance of strong data protection for all organizations handling sensitive customer data. Understanding the T-Mobile data breach is a crucial step in protecting your personal information. Learn more about data security best practices and advocate for stronger data protection measures from your service providers. Preventing data breaches requires a multi-faceted approach encompassing robust technology, rigorous employee training, and a proactive commitment to data security.

Featured Posts
-
 Papa Francesco E Il Conclave Analisi Dei Cardinali Scelti
May 07, 2025
Papa Francesco E Il Conclave Analisi Dei Cardinali Scelti
May 07, 2025 -
 Boston Celtics Blown Lead 4 Crucial Takeaways From Cavs Victory
May 07, 2025
Boston Celtics Blown Lead 4 Crucial Takeaways From Cavs Victory
May 07, 2025 -
 Ralph Macchio Offers My Cousin Vinny Reboot Update Joe Pescis Involvement Discussed
May 07, 2025
Ralph Macchio Offers My Cousin Vinny Reboot Update Joe Pescis Involvement Discussed
May 07, 2025 -
 Experience The Return Of Arcade Mode In Nhl 25
May 07, 2025
Experience The Return Of Arcade Mode In Nhl 25
May 07, 2025 -
 Zvabliva Rianna Fotosesiya U Rozhevomu Merezhivi
May 07, 2025
Zvabliva Rianna Fotosesiya U Rozhevomu Merezhivi
May 07, 2025
Latest Posts
-
 Fan Question For Donovan Mitchell On Talking Heads With Ashley Holder
May 07, 2025
Fan Question For Donovan Mitchell On Talking Heads With Ashley Holder
May 07, 2025 -
 Updated Injury Report Cavaliers Vs Grizzlies March 14th
May 07, 2025
Updated Injury Report Cavaliers Vs Grizzlies March 14th
May 07, 2025 -
 Playoff Stars How Mitchell And Brunson Are Proving Their Worth
May 07, 2025
Playoff Stars How Mitchell And Brunson Are Proving Their Worth
May 07, 2025 -
 Royal Air Maroc And Fespaco A Renewed Partnership For African Cinema
May 07, 2025
Royal Air Maroc And Fespaco A Renewed Partnership For African Cinema
May 07, 2025 -
 Betting On The Cavaliers Vs Pacers Your Guide To The Eastern Conference Semifinals
May 07, 2025
Betting On The Cavaliers Vs Pacers Your Guide To The Eastern Conference Semifinals
May 07, 2025
