Office365 Security Flaw Leads To Millions In Losses For Executives
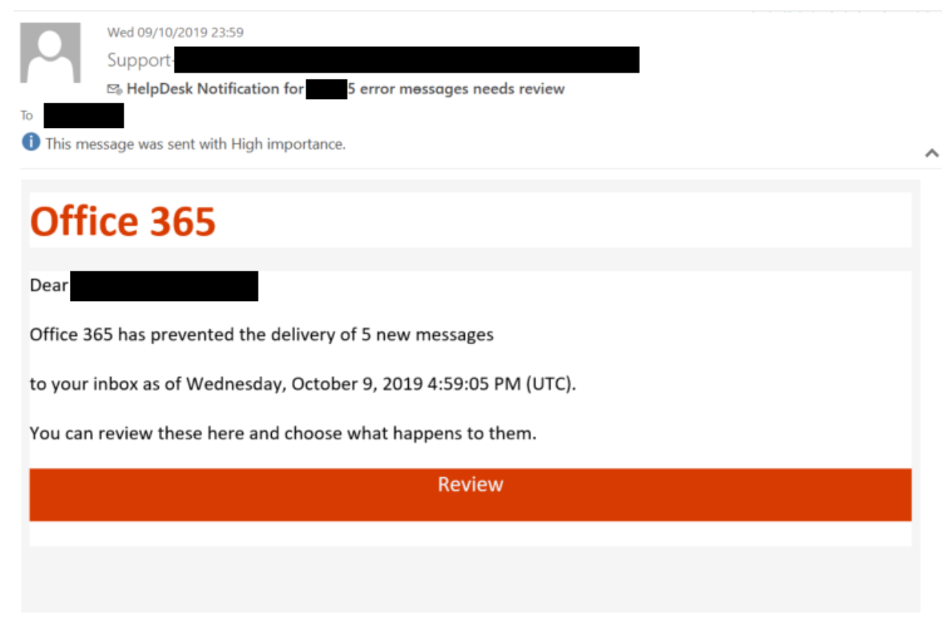
Table of Contents
Understanding the Office365 Security Flaw(s)
The term "Office365 security flaw" encompasses a broad range of vulnerabilities that malicious actors exploit to gain unauthorized access to sensitive data. These flaws aren't always sophisticated zero-day exploits; often, they leverage basic human error or poorly configured systems. Let's explore some key vulnerabilities:
-
Phishing Attacks: These remain the most prevalent attack vector. Sophisticated phishing emails, often mimicking legitimate communications from trusted sources, trick unsuspecting employees into revealing credentials or downloading malware. The attacker then uses these credentials to access the victim's Office365 account, granting access to emails, files, and other sensitive data.
-
Compromised Credentials: Weak or reused passwords, combined with a lack of multi-factor authentication (MFA), create easy entry points for attackers. Credential stuffing, where attackers use stolen credentials from other data breaches to try accessing Office365 accounts, is a significant threat.
-
API Vulnerabilities: Application Programming Interfaces (APIs) are often overlooked security weak points. If not properly secured, APIs can allow attackers to bypass standard authentication methods and access sensitive data directly.
Examples of Real-World Scenarios:
-
An employee clicks a malicious link in a phishing email, granting attackers access to their inbox and subsequently the entire organization's email system.
-
An attacker uses stolen credentials obtained from a separate data breach to access an Office365 account, exfiltrating sensitive financial data.
-
An unpatched vulnerability in an Office365 API allows an attacker to gain unauthorized access to company files stored in SharePoint or OneDrive.
-
Common Attack Vectors:
- Phishing emails with malicious attachments or links.
- Brute-force and credential stuffing attacks.
- Exploiting vulnerabilities in third-party applications integrated with Office365.
- Social engineering tactics to manipulate employees into revealing sensitive information.
-
Types of Data Breaches:
- Email compromise leading to financial fraud or intellectual property theft.
- Data exfiltration of sensitive customer information, violating privacy regulations like GDPR.
- Access to confidential business documents and strategic plans.
-
Specific Examples of Known Vulnerabilities: (Note: Specific vulnerability details are frequently patched and change rapidly. Consult Microsoft's Security Response Center for the most up-to-date information).
The Financial Ramifications of Office365 Breaches for Executives
The financial fallout from an Office365 security breach can be catastrophic. The costs extend far beyond the immediate remediation efforts:
-
Direct Costs: Legal fees for data breach investigations and notification, remediation costs to restore systems and data, and potentially hefty regulatory fines (like GDPR penalties) can quickly reach into the millions.
-
Indirect Costs: Reputational damage leading to lost customers and investor confidence, decreased productivity due to system downtime and investigations, and the cost of restoring damaged trust with clients and partners can cripple long-term growth.
-
Bullet Points:
- Data recovery and incident response can cost tens of thousands, even hundreds of thousands of dollars.
- Negative impact on stock prices and shareholder value can result in significant financial losses.
- Legal liabilities and lawsuits following a breach can lead to multi-million dollar settlements.
Best Practices for Preventing Office365 Security Breaches
Proactive security measures are crucial in preventing costly Office365 security flaws. Here are vital steps executives and IT teams can implement:
-
Robust Authentication: Implement multi-factor authentication (MFA) for all users. This adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain passwords. Enforce strong password policies, including password complexity requirements and regular password changes.
-
Employee Training: Invest in comprehensive security awareness training to educate employees about phishing scams, social engineering tactics, and safe online practices. Regular simulated phishing exercises can help identify vulnerabilities within the workforce.
-
Advanced Threat Protection: Utilize advanced threat protection solutions offered by Microsoft or reputable third-party vendors. These solutions can detect and prevent sophisticated attacks that bypass traditional security measures.
-
Regular Security Audits: Conduct regular security audits to identify potential vulnerabilities and ensure that security controls are effective.
-
Bullet Points:
- Implement and enforce strong password policies, including MFA for all users.
- Regularly update Office365 software and security patches.
- Conduct regular security awareness training for employees, including simulated phishing attacks.
- Utilize advanced security tools such as anti-malware and intrusion detection systems.
- Implement data loss prevention (DLP) measures to control sensitive data movement.
Case Studies: Real-World Examples of Office365 Security Failures
While specific details of many breaches remain confidential due to NDAs, numerous publicized instances highlight the devastating consequences of insufficient security. (Note: Including specific, well-sourced case studies here would significantly strengthen this section. Research reputable cybersecurity news sources for examples).
Conclusion: Protecting Your Business from Office365 Security Flaws
The potential financial impact of Office365 security flaws cannot be overstated. The cost of a breach extends far beyond immediate remediation, impacting reputation, customer trust, and long-term profitability. By proactively implementing the security measures discussed above – including robust authentication, employee training, and advanced threat protection – executives can significantly reduce their risk and protect their organizations from the devastating consequences of these vulnerabilities. Don't wait for a breach to occur; take immediate action to secure your Office365 environment and safeguard your business. For further information on bolstering your Office365 security, explore Microsoft's security documentation and consider engaging a cybersecurity professional for a comprehensive security assessment.

Featured Posts
-
 Lyudi Lyubyat Schekotat Nervy Fedor Lavrov O Pavle I Trillerakh I Refleksii
May 24, 2025
Lyudi Lyubyat Schekotat Nervy Fedor Lavrov O Pavle I Trillerakh I Refleksii
May 24, 2025 -
 Ronan Farrow And Mia Farrows Future A Comeback Story
May 24, 2025
Ronan Farrow And Mia Farrows Future A Comeback Story
May 24, 2025 -
 Finding Bbc Big Weekend 2025 Sefton Park Tickets
May 24, 2025
Finding Bbc Big Weekend 2025 Sefton Park Tickets
May 24, 2025 -
 Apple Stock Update Q2 Financial Report And Market Impact
May 24, 2025
Apple Stock Update Q2 Financial Report And Market Impact
May 24, 2025 -
 Your Guide To Obtaining Bbc Radio 1 Big Weekend Tickets
May 24, 2025
Your Guide To Obtaining Bbc Radio 1 Big Weekend Tickets
May 24, 2025
Latest Posts
-
 Guilty Verdict In Columbus Child Sex Crimes Trial
May 24, 2025
Guilty Verdict In Columbus Child Sex Crimes Trial
May 24, 2025 -
 Columbus Child Sex Crime Case Ends In Guilty Verdict
May 24, 2025
Columbus Child Sex Crime Case Ends In Guilty Verdict
May 24, 2025 -
 Sylvester Stallone Suits Up For Tulsa King Season 3
May 24, 2025
Sylvester Stallone Suits Up For Tulsa King Season 3
May 24, 2025 -
 Best Memorial Day Deals 2025 Shopping Editors Top Choices
May 24, 2025
Best Memorial Day Deals 2025 Shopping Editors Top Choices
May 24, 2025 -
 Memorial Day 2025 Expert Selected Sales And Deals
May 24, 2025
Memorial Day 2025 Expert Selected Sales And Deals
May 24, 2025
