Office365 Security Failure Leads To Millions In Losses For Executives

Table of Contents
Common Office365 Security Vulnerabilities Leading to Financial Losses
Many organizations mistakenly believe that migrating to the cloud inherently solves their security concerns. However, Office365, like any cloud platform, requires proactive and robust security measures. Several common vulnerabilities frequently lead to significant financial losses.
Phishing and Social Engineering Attacks
Phishing scams remain a primary vector for Office365 security failures. Attackers cleverly craft emails mimicking legitimate communications, tricking employees into revealing sensitive information like usernames, passwords, or clicking malicious links. These attacks exploit weak passwords and employee negligence, gaining access to sensitive data residing within Office365, including customer information, financial records, and intellectual property.
Statistics reveal a frightening trend: a significant percentage of successful data breaches stem from successful phishing attempts targeting Office365 users. The financial repercussions are substantial, encompassing:
- Data recovery costs: Restoring compromised data can be incredibly expensive, involving IT specialists, forensic analysis, and potentially rebuilding entire systems.
- Legal fees: Data breaches often trigger investigations and lawsuits, incurring hefty legal fees for defense and potential settlements.
- Reputational damage: Loss of customer trust and damage to brand reputation can lead to a significant decline in revenue and market share.
Best practices for mitigating phishing attacks:
- Regular security awareness training: Educate employees on identifying and avoiding phishing attempts.
- Implement robust email filtering: Utilize advanced spam filtering and anti-phishing solutions.
- Use strong, unique passwords: Encourage employees to create strong passwords and change them regularly.
- Enable multi-factor authentication (MFA): This adds an extra layer of security, even if credentials are compromised.
Weak or Shared Passwords
Using weak passwords or sharing passwords among employees dramatically increases the risk of an Office365 security failure. Weak passwords are easily cracked using readily available tools, providing attackers with direct access to sensitive business data stored within Office365. The financial implications of a password breach are severe:
- Data restoration costs: Recovering stolen data can be time-consuming and expensive.
- Regulatory fines: Non-compliance with data protection regulations (like GDPR or CCPA) can result in substantial financial penalties.
- Loss of customer trust: A data breach can severely damage an organization's reputation, leading to lost business.
Password management best practices:
- Enforce strong password policies: Require passwords with a minimum length, complexity, and regular changes.
- Implement multi-factor authentication (MFA): MFA adds a second layer of security, making it significantly harder for attackers to gain access even with a stolen password.
- Utilize password management tools: These tools help generate and securely store strong, unique passwords.
Lack of Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a crucial security measure that significantly reduces the risk of unauthorized access, even if an attacker obtains a username and password. By requiring a second form of authentication (e.g., a code from a mobile app or a security token), MFA adds an essential layer of protection. The financial impact of not implementing MFA is substantial:
- Increased vulnerability to ransomware attacks: Without MFA, attackers can easily access sensitive data and encrypt it, demanding a ransom for its release.
- Higher costs associated with data breaches: The financial fallout from a data breach, including legal fees, regulatory fines, and reputational damage, is significantly amplified without MFA.
Implementing MFA in Office365:
- Choose the right MFA method: Several options exist, including authenticator apps, security keys, and SMS codes.
- Enforce MFA for all users: Ensure all users, including executives and administrators, are required to use MFA.
- Monitor MFA usage and logs: Regularly review MFA logs to identify and address any anomalies.
Unpatched Software and Vulnerabilities
Out-of-date software creates significant security vulnerabilities, leaving organizations susceptible to attacks. Attackers actively scan for and exploit known vulnerabilities in Office365 applications to gain unauthorized access and potentially deploy ransomware or exfiltrate sensitive data. The financial consequences of failing to maintain up-to-date software are severe:
- Increased risk of ransomware infections: Outdated software makes it easier for ransomware to infect systems.
- Data breaches: Vulnerabilities in unpatched software can be exploited to access and steal sensitive information.
- Compliance violations: Failure to maintain up-to-date software can lead to regulatory non-compliance and associated fines.
Best practices for software updates:
- Implement automated patching solutions: Automate software updates to ensure systems are always up-to-date.
- Conduct regular security risk assessments: Identify and address potential vulnerabilities before attackers can exploit them.
- Stay informed about security updates: Monitor security advisories and patch your software promptly.
Inadequate Data Loss Prevention (DLP) Measures
Effective data loss prevention (DLP) measures are crucial for preventing sensitive data from leaving the organization’s control. Inadequate DLP can lead to costly data breaches, resulting in severe financial consequences:
- Regulatory fines: Non-compliance with data protection regulations can lead to substantial penalties.
- Reputational damage: A data breach can severely harm an organization's reputation, leading to lost customers and business.
- Legal costs: Lawsuits from affected individuals or organizations can significantly impact the financial health of the company.
Implementing effective DLP measures:
- Data classification: Categorize data based on sensitivity and apply appropriate security controls.
- Data encryption: Encrypt sensitive data both in transit and at rest.
- Access control: Restrict access to sensitive data based on the principle of least privilege.
- Data loss prevention tools: Utilize Office365's built-in DLP tools and consider third-party solutions.
Executive Liability and Responsibility in Office365 Security Failures
Executives bear significant legal and financial responsibility for ensuring adequate Office365 security measures are in place. In the event of a data breach or security failure, executives can face personal liability, including:
- Financial penalties: Fines imposed by regulatory bodies for non-compliance.
- Lawsuits: Lawsuits from affected individuals or organizations.
- Reputational damage: Damage to personal and professional reputation.
Mitigating executive liability:
- Implement robust security policies and procedures: Develop and enforce comprehensive security policies and procedures.
- Ensure compliance with relevant regulations: Stay informed about and comply with relevant data protection regulations (e.g., GDPR, CCPA).
- Invest in cybersecurity insurance: Protect against potential financial losses resulting from data breaches.
Conclusion
Office365 security failures are not merely technical issues; they represent significant financial risks with far-reaching consequences for executives and their organizations. Neglecting security best practices can lead to substantial financial losses, legal battles, and irreparable reputational damage.
Call to Action: Protect your organization and mitigate the risk of costly Office365 security failures. Implement robust security measures, including strong passwords, multi-factor authentication, regular software updates, and comprehensive data loss prevention strategies. Don't wait for a catastrophic Office365 data breach – take proactive steps to secure your valuable data and protect your bottom line. Invest in comprehensive Office365 security solutions today.

Featured Posts
-
 Lizzo Sparks Controversy Comparing Britney Spears To Janet Jackson
May 04, 2025
Lizzo Sparks Controversy Comparing Britney Spears To Janet Jackson
May 04, 2025 -
 Concert Spotlight Lizzos Stunning Curves In Los Angeles
May 04, 2025
Concert Spotlight Lizzos Stunning Curves In Los Angeles
May 04, 2025 -
 45 000 Rare Book Unearthed In Bookstore
May 04, 2025
45 000 Rare Book Unearthed In Bookstore
May 04, 2025 -
 Carneys Plan Reshaping The Economy For A Generation
May 04, 2025
Carneys Plan Reshaping The Economy For A Generation
May 04, 2025 -
 Ruth Buzzi Sesame Street Laugh In A Celebration Of Her Life And Career
May 04, 2025
Ruth Buzzi Sesame Street Laugh In A Celebration Of Her Life And Career
May 04, 2025
Latest Posts
-
 Holi Weather Forecast For West Bengal Expect High Tide And Heat
May 04, 2025
Holi Weather Forecast For West Bengal Expect High Tide And Heat
May 04, 2025 -
 Me T Department Predicts High Tide And Temperature In West Bengal For Holi
May 04, 2025
Me T Department Predicts High Tide And Temperature In West Bengal For Holi
May 04, 2025 -
 West Bengal Holi Weather High Tide And Temperature Forecast
May 04, 2025
West Bengal Holi Weather High Tide And Temperature Forecast
May 04, 2025 -
 Wb Weather Update Holi Brings High Tide And Temperature Warnings
May 04, 2025
Wb Weather Update Holi Brings High Tide And Temperature Warnings
May 04, 2025 -
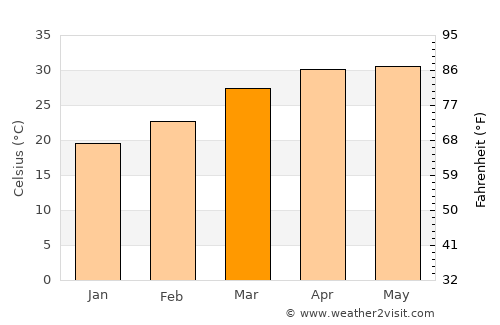 Rising Temperatures In Kolkata March Weather Update And Outlook
May 04, 2025
Rising Temperatures In Kolkata March Weather Update And Outlook
May 04, 2025
