Office365 Security Breach: FBI Investigation Into Multi-Million Dollar Theft

Table of Contents
The Scale of the Office365 Security Breach
This Office365 security breach represents a significant financial and reputational blow to the affected organization. The sheer scale of the data theft and its potential long-term consequences demand immediate attention.
Financial Losses
The estimated financial losses incurred due to this breach are staggering. While precise figures remain undisclosed pending the ongoing FBI investigation, sources suggest a loss in the multi-million dollar range.
- Millions of dollars in financial assets compromised: This includes direct monetary losses from fraudulent transactions and the theft of valuable financial data.
- Potential impact on shareholder value and company reputation: The news of a significant data breach can severely damage a company's reputation, leading to decreased investor confidence and a decline in share prices.
- Losses extend beyond immediate financial impact to include legal fees and remediation costs: The costs associated with legal battles, regulatory fines, and the remediation of compromised systems can significantly inflate the overall financial burden. This includes the cost of credit monitoring services for affected customers and the expense of hiring cybersecurity experts to investigate and secure systems.
Data Breached
The breadth of sensitive data compromised in this Office365 security breach is equally concerning. The attackers gained access to a wide range of crucial information.
- Customer data (PII, addresses, financial info): Personally Identifiable Information (PII), including names, addresses, and financial details, puts customers at significant risk of identity theft and fraud.
- Internal company documents and intellectual property: The theft of confidential internal documents and intellectual property can cause irreparable damage to the company's competitive advantage and future prospects.
- Employee information, potentially impacting HR and payroll systems: Access to employee information can lead to various forms of identity theft, payroll fraud, and disruptions to HR operations.
FBI Investigation and Response
The FBI's swift response to this Office365 security breach demonstrates the seriousness of the situation. A multi-agency task force is likely involved in the investigation.
Investigative Actions
The FBI is employing a multi-pronged approach to investigate this complex case.
- Cybersecurity experts analyzing compromised systems: Specialized teams are meticulously examining the compromised systems to understand the attack's methods, scope, and the extent of data exfiltration.
- Tracing the origins and methods of the attack: Investigators are working to identify the perpetrators, their location, and the techniques used to breach the Office365 environment. This often involves analyzing network logs, server data, and malware samples.
- Working to identify and apprehend the perpetrators: The FBI is actively pursuing leads and utilizing its resources to bring those responsible for this crime to justice.
Law Enforcement Collaboration
This type of sophisticated cybercrime often requires international collaboration.
- Partnerships with other law enforcement agencies (specify countries if known): The FBI likely collaborates with international counterparts to track down perpetrators who may be operating across borders.
- Information sharing to combat similar cybercrimes globally: Sharing information on attack methods, attacker tactics, and vulnerabilities helps law enforcement agencies worldwide to better prepare for and prevent future incidents.
Vulnerabilities Exploited in the Office365 Security Breach
Understanding the vulnerabilities exploited in this breach is crucial for preventing future incidents. The attackers likely utilized a combination of techniques.
Phishing and Social Engineering
Phishing attacks remain a highly effective method for gaining initial access to corporate systems.
- Exploitation of weak passwords and credential stuffing: Attackers often utilize lists of stolen credentials (credential stuffing) or exploit weak passwords to gain access to accounts.
- Use of convincing phishing emails to trick employees into revealing credentials: Sophisticated phishing campaigns can bypass security awareness training, leading to employees inadvertently compromising their credentials.
Software Vulnerabilities
Outdated software and unpatched vulnerabilities create significant security weaknesses.
- Unpatched software or outdated security protocols: Failing to regularly update software leaves systems vulnerable to known exploits.
- Lack of multi-factor authentication (MFA): Multi-factor authentication (MFA) adds an extra layer of security, making it significantly harder for attackers to gain access even if they obtain passwords.
- Inadequate employee training on cybersecurity best practices: Employee training is paramount in reducing the risk of phishing attacks and other social engineering techniques.
Preventing Future Office365 Security Breaches
Proactive measures are essential in preventing future Office365 security breaches.
Strengthened Security Protocols
Organizations must implement robust security protocols to mitigate the risk of future attacks.
- Implementing multi-factor authentication (MFA) for all accounts: MFA adds an essential layer of protection.
- Regular security audits and penetration testing: Regular assessments help identify vulnerabilities before attackers can exploit them.
- Robust employee training programs focusing on cybersecurity awareness: Educating employees about phishing techniques and cybersecurity best practices is essential.
Regular Software Updates
Keeping software up-to-date is crucial.
- Automatic update settings enabled for all Office365 applications: Enable automatic updates to ensure systems are protected against the latest vulnerabilities.
- Monitoring for and addressing any software vulnerabilities promptly: Regularly monitor for security updates and address any vulnerabilities immediately.
Conclusion
The FBI's investigation into this multi-million dollar Office365 security breach serves as a stark reminder of the ever-present threat of cybercrime. The scale of this data theft underscores the critical need for proactive security measures to protect sensitive information and prevent similar incidents. By implementing robust security protocols, including multi-factor authentication, regular software updates, and comprehensive employee training, organizations can significantly reduce their vulnerability to Office365 security breaches and safeguard their valuable data. Don't wait for a devastating Office365 security breach to strike; take action today to secure your organization's future. Invest in comprehensive cybersecurity measures to protect your business from this growing threat. Strengthen your Office365 security now and prevent becoming another statistic.

Featured Posts
-
 Manila Bay A Vibrant Ecosystem How Long Will It Last
May 30, 2025
Manila Bay A Vibrant Ecosystem How Long Will It Last
May 30, 2025 -
 Heute In Augsburg Der M Net Firmenlauf Ergebnisse And Bilder
May 30, 2025
Heute In Augsburg Der M Net Firmenlauf Ergebnisse And Bilder
May 30, 2025 -
 Sierra Leone Immigration Chief Removed From Post Official Statement
May 30, 2025
Sierra Leone Immigration Chief Removed From Post Official Statement
May 30, 2025 -
 Laurent Jacobelli Un Portrait Du Depute De La Moselle A L Assemblee Nationale
May 30, 2025
Laurent Jacobelli Un Portrait Du Depute De La Moselle A L Assemblee Nationale
May 30, 2025 -
 Taylor Swift Ticket Sales Ticketmaster Improves Queue Transparency
May 30, 2025
Taylor Swift Ticket Sales Ticketmaster Improves Queue Transparency
May 30, 2025
Latest Posts
-
 Rebuilding After The Inferno The Texas Panhandles Post Wildfire Recovery
May 31, 2025
Rebuilding After The Inferno The Texas Panhandles Post Wildfire Recovery
May 31, 2025 -
 Out Of Control Wildfires In Eastern Manitoba A Look At The Ongoing Emergency Response
May 31, 2025
Out Of Control Wildfires In Eastern Manitoba A Look At The Ongoing Emergency Response
May 31, 2025 -
 Deadly Wildfires Continue To Threaten Eastern Manitoba Update On Firefighting Efforts
May 31, 2025
Deadly Wildfires Continue To Threaten Eastern Manitoba Update On Firefighting Efforts
May 31, 2025 -
 One Year After The Texas Panhandle Wildfire Assessing The Damage And Progress
May 31, 2025
One Year After The Texas Panhandle Wildfire Assessing The Damage And Progress
May 31, 2025 -
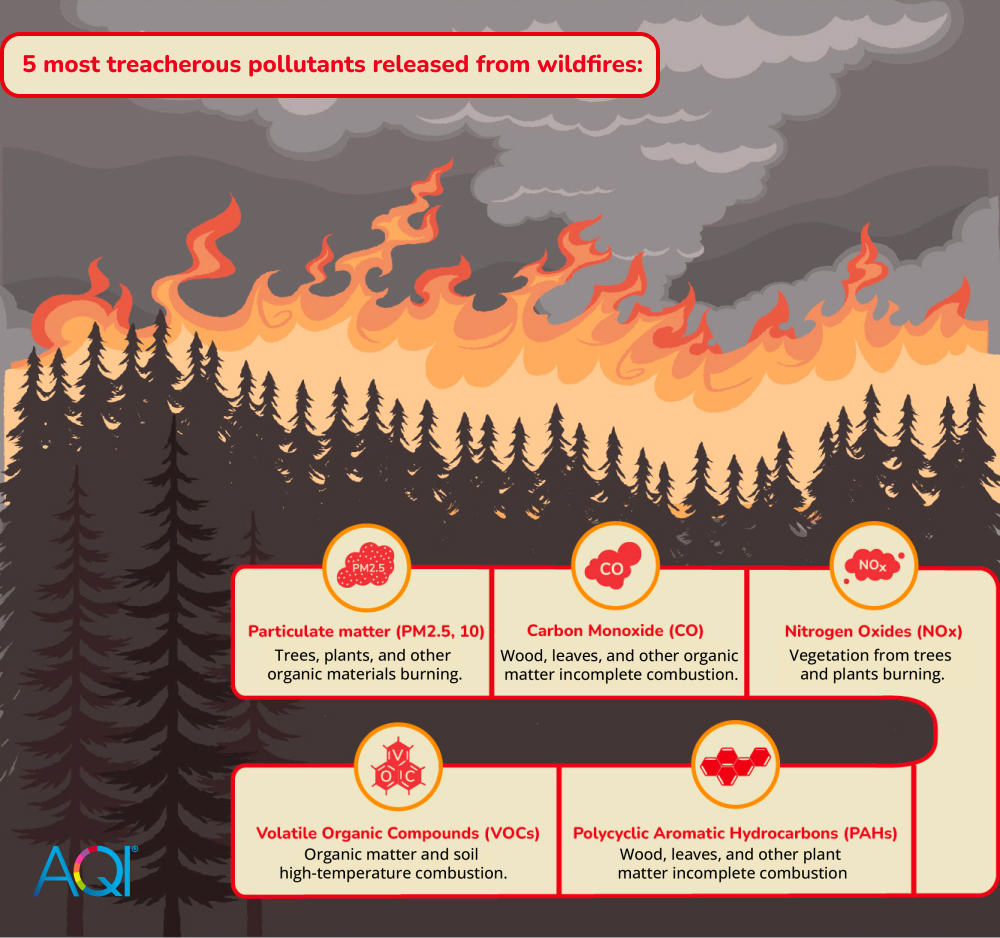 Respiratory Health Concerns Rise As Canadian Wildfires Affect Minnesota Air
May 31, 2025
Respiratory Health Concerns Rise As Canadian Wildfires Affect Minnesota Air
May 31, 2025
