Millions Stolen Through Sophisticated Office365 Executive Account Hacking
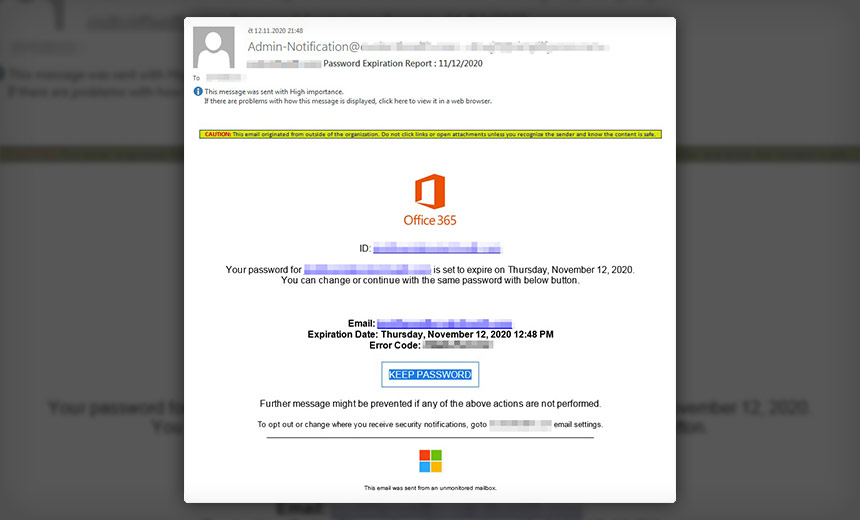
Table of Contents
Methods Employed in Office365 Executive Account Hacking
Cybercriminals utilize various sophisticated methods to compromise Office365 executive accounts. Understanding these tactics is the first step in building a robust defense.
Spear Phishing Attacks
Spear phishing is a highly targeted form of phishing, designed to appear legitimate and bypass security measures. These attacks often mimic trusted sources or individuals known to the executive, using sophisticated social engineering techniques to build trust.
- Sophisticated social engineering techniques: Attackers meticulously research their targets, gathering information from social media, company websites, and other public sources to personalize their emails and increase the likelihood of success.
- Use of malicious links or attachments: Emails often contain malicious links that redirect victims to phishing websites designed to steal credentials or download malware onto their systems. Attachments may contain malicious macros or other harmful code.
- Examples of spear phishing email subject lines and content: Subject lines might mimic urgent business matters, such as "Important Contract," "Financial Report," or "Confidential Information." The email body will be tailored to the recipient, referencing specific projects, colleagues, or internal company information.
Credential Stuffing
Credential stuffing leverages stolen credentials from other data breaches to attempt logins to Office365 accounts. Attackers purchase or obtain lists of usernames and passwords from the dark web and use automated tools to test them against various platforms, including Office365.
- The role of dark web marketplaces: These underground marketplaces facilitate the buying and selling of stolen credentials, making it relatively easy for attackers to obtain large lists of usernames and passwords.
- The importance of strong, unique passwords and multi-factor authentication: Using strong, unique passwords for each account and enabling multi-factor authentication (MFA) significantly reduces the effectiveness of credential stuffing attacks.
- How password managers can improve security: Password managers generate strong, unique passwords and securely store them, eliminating the need for users to remember complex credentials.
Exploiting Vulnerabilities
Cybercriminals actively search for and exploit known security flaws in Office365 or related applications. This often involves leveraging zero-day exploits – vulnerabilities that are unknown to the software vendor.
- Importance of regularly updating software and applying security patches: Regularly updating software and applying security patches is critical to mitigating the risk of exploitation.
- The role of zero-day exploits and their impact on security: Zero-day exploits pose a significant threat as they are unknown to the vendor, leaving systems vulnerable until a patch is developed and deployed.
- The effectiveness of vulnerability scanning and penetration testing: Regular vulnerability scanning and penetration testing can identify and address security weaknesses before they can be exploited by attackers.
Compromised Third-Party Applications
Attackers can gain access to Office365 accounts through unsecured or vulnerable third-party applications integrated with the platform. These applications may have weak security measures or vulnerabilities that attackers can exploit.
- The importance of vetting third-party applications before integration: Thoroughly vetting third-party applications before integration is crucial to ensuring their security.
- The need for regular security audits of integrated applications: Regular security audits of integrated applications help identify and address potential vulnerabilities.
- Minimizing access permissions for third-party apps: Granting only the necessary permissions to third-party applications limits the potential damage in case of a compromise.
Devastating Consequences of Office365 Executive Account Hacking
The consequences of a successful Office365 executive account hacking can be devastating, impacting various aspects of an organization.
Financial Losses
The direct financial impact of these attacks can be significant.
- Examples of financial losses: This includes direct theft of funds, fraudulent transactions, costly recovery efforts, and the expense of dealing with legal ramifications.
- The impact of reputational damage: Reputational damage can lead to a loss of investor confidence and decreased business opportunities.
Reputational Damage
A data breach can severely damage an organization's reputation.
- The negative impact on brand image: Loss of customer trust, decreased brand loyalty, and negative media coverage can have long-term consequences.
- The importance of transparency: Transparency and swift communication are crucial in mitigating reputational damage.
Legal and Regulatory Penalties
Organizations may face significant legal and regulatory penalties.
- Examples of relevant data protection regulations: Non-compliance with regulations like GDPR, CCPA, and others can result in substantial fines.
- The cost of legal proceedings: Legal proceedings and potential settlements can significantly add to the financial burden.
Intellectual Property Theft
The theft of valuable intellectual property can have long-term consequences.
- The long-term impact on business competitiveness: Loss of trade secrets, designs, and other confidential information can severely impact a company's competitiveness.
- The difficulty of recovery: Recovering stolen intellectual property can be extremely difficult and costly.
Protecting Your Organization from Office365 Executive Account Hacking
Implementing robust security measures is crucial in preventing Office365 executive account hacking.
Implementing Multi-Factor Authentication (MFA)
MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
Regular Security Awareness Training
Educating employees about phishing techniques and safe online practices is essential in preventing attacks.
Enforce Strong Password Policies
Requiring complex and unique passwords for all accounts minimizes the risk of credential stuffing attacks.
Regular Security Audits and Penetration Testing
Regular audits and penetration testing identify vulnerabilities and weaknesses in your systems.
Employing Advanced Threat Protection (ATP)
ATP solutions offer advanced capabilities to detect and prevent malicious activities.
Incident Response Plan
Having a well-defined plan in place to handle a security breach is crucial for minimizing the impact.
Conclusion
Sophisticated Office365 executive account hacking poses a significant threat to businesses worldwide. The financial, reputational, and legal consequences can be devastating. By understanding the methods employed by cybercriminals and implementing robust security measures, organizations can significantly reduce their risk. Investing in multi-factor authentication, security awareness training, and advanced threat protection is crucial in safeguarding against this growing threat. Don't wait until it's too late – take proactive steps to protect your organization from Office365 executive account hacking and secure your valuable data. Learn more about strengthening your Office 365 security today!

Featured Posts
-
 The Long Shadow Of A Giants Legend
May 14, 2025
The Long Shadow Of A Giants Legend
May 14, 2025 -
 Kralj Tenisa Kako Je Dokovic Srusio Federerove Rekorde
May 14, 2025
Kralj Tenisa Kako Je Dokovic Srusio Federerove Rekorde
May 14, 2025 -
 Celine Dion Ne Eurovizion 2025 A Do Te Pranoje Diva
May 14, 2025
Celine Dion Ne Eurovizion 2025 A Do Te Pranoje Diva
May 14, 2025 -
 Alexis Kohler Quitte L Elysee Analyse De L Impact Sur La Presidence Macron
May 14, 2025
Alexis Kohler Quitte L Elysee Analyse De L Impact Sur La Presidence Macron
May 14, 2025 -
 Wegmans Product Recall Action Needed For Braised Beef With Vegetables
May 14, 2025
Wegmans Product Recall Action Needed For Braised Beef With Vegetables
May 14, 2025
