Millions In Losses: Insider Threat Or Sophisticated Office365 Breach?
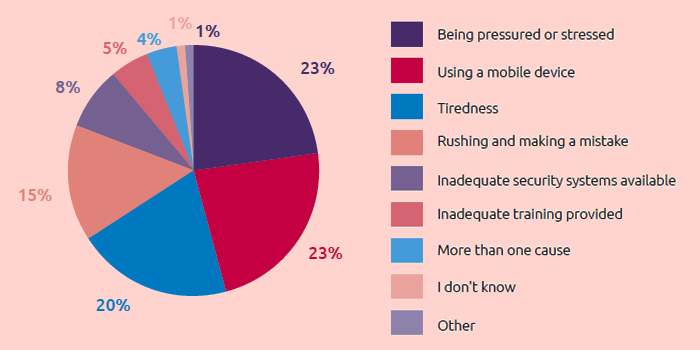
Table of Contents
Identifying an Insider Threat
Identifying an insider threat requires a keen eye for anomalies and a deep understanding of employee behavior. Effective Insider Threat Detection relies on a multi-faceted approach.
Unusual Access Patterns
Anomaly detection is crucial in identifying insider threats. Look for inconsistencies in user activity:
- Login times and locations: Access from unusual geographic locations or outside of regular work hours warrants investigation. Use User and Entity Behavior Analytics (UEBA) tools to establish baselines and identify deviations.
- Increased file downloads or access to sensitive data: A sudden spike in downloads of sensitive files or access attempts to restricted data points to potential malicious activity.
- Suspicious access attempts: Multiple failed login attempts or attempts to access accounts outside of authorized access patterns are strong indicators.
Privileged Account Abuse
Unauthorized access to privileged accounts is a major red flag. Robust Privileged Access Management (PAM) is essential:
- Administrative account access: Any unauthorized access to administrative accounts should trigger an immediate alert. Account monitoring is critical here.
- Permission changes: Suspicious changes to user permissions or group memberships, especially those granting broad access, require thorough investigation.
- Data exfiltration: Monitor for unusual data transfers or attempts to exfiltrate data via privileged accounts.
Behavioral Indicators
Changes in employee behavior can be subtle but significant. Behavioral analytics can help:
- Changes in demeanor: Increased stress, secrecy, or avoidance of colleagues could signal potential insider threat activity. Employee monitoring, however, should always be conducted ethically and within legal boundaries.
- Dissatisfaction or grievances: Employees with unresolved grievances or dissatisfaction with the company may be more likely to engage in malicious activity. A thorough risk assessment should be undertaken to identify potentially vulnerable employees.
- Financial difficulties or personal issues: Financial distress or personal problems can motivate employees to commit insider threats.
Recognizing a Sophisticated Office365 Breach
Sophisticated Office365 breaches often utilize advanced techniques to bypass security measures.
Advanced Phishing and Social Engineering
Modern phishing attacks are far from simple. They employ sophisticated techniques:
- MFA bypass: Attackers are increasingly skilled at bypassing multi-factor authentication (MFA) through techniques like phishing for MFA codes or exploiting vulnerabilities in MFA systems. Phishing detection systems should be up-to-date and regularly tested.
- Social engineering tactics: Attackers utilize sophisticated social engineering techniques to manipulate users into revealing credentials or clicking malicious links. Training employees to recognize and report phishing attempts is crucial.
- Exploiting application vulnerabilities: Attackers actively search for and exploit vulnerabilities in Office 365 applications themselves. Regular updates and patching are non-negotiable. Staying informed about the latest threats is also vital; understanding the techniques used by Advanced Persistent Threats (APTs) is key.
Exploiting Zero-Day Vulnerabilities
Exploiting zero-day vulnerabilities is a hallmark of highly sophisticated attacks:
- Unpatched vulnerabilities: Attackers leverage newly discovered vulnerabilities before patches are released, requiring proactive vulnerability management.
- Malware and ransomware: Infection often involves malware or ransomware designed to steal data or disrupt operations. Malware analysis and ransomware detection are essential components of a strong security posture.
- Account compromise for further attacks: Compromised email accounts are frequently used as springboards to access other systems and accounts within the organization.
Lateral Movement and Data Exfiltration
Successful breaches often involve moving laterally within the network:
- Accessing sensitive data: Attackers move through the network to access sensitive data, requiring robust lateral movement detection capabilities.
- Using compromised accounts: Compromised accounts provide access to other systems and data.
- Exfiltrating data: Data exfiltration commonly occurs through cloud storage services or external servers. Data Loss Prevention (DLP) solutions are vital in preventing this. Leveraging threat intelligence feeds can help identify and mitigate potential threats before they compromise your network.
Distinguishing Factors
Differentiating between insider threats and external breaches requires careful analysis. Threat hunting and robust incident response plans are vital. The subtle differences in attack vectors and techniques often require advanced digital forensics expertise. Attribution can be challenging, requiring meticulous investigation to determine the source and method of the breach.
Conclusion
Protecting your organization from millions in losses requires a multi-layered approach to cybersecurity. While both insider threats and sophisticated Office 365 breaches pose significant risks, understanding the key differences – from unusual access patterns to advanced phishing techniques and lateral movement – is crucial for effective mitigation. Implement strong Office 365 security measures, including robust multi-factor authentication, advanced threat protection, regular security awareness training, and proactive threat hunting, to effectively mitigate the risk of both insider threats and sophisticated Office 365 breaches. Investing in proactive security measures is far less costly than recovering from a major data breach.

Featured Posts
-
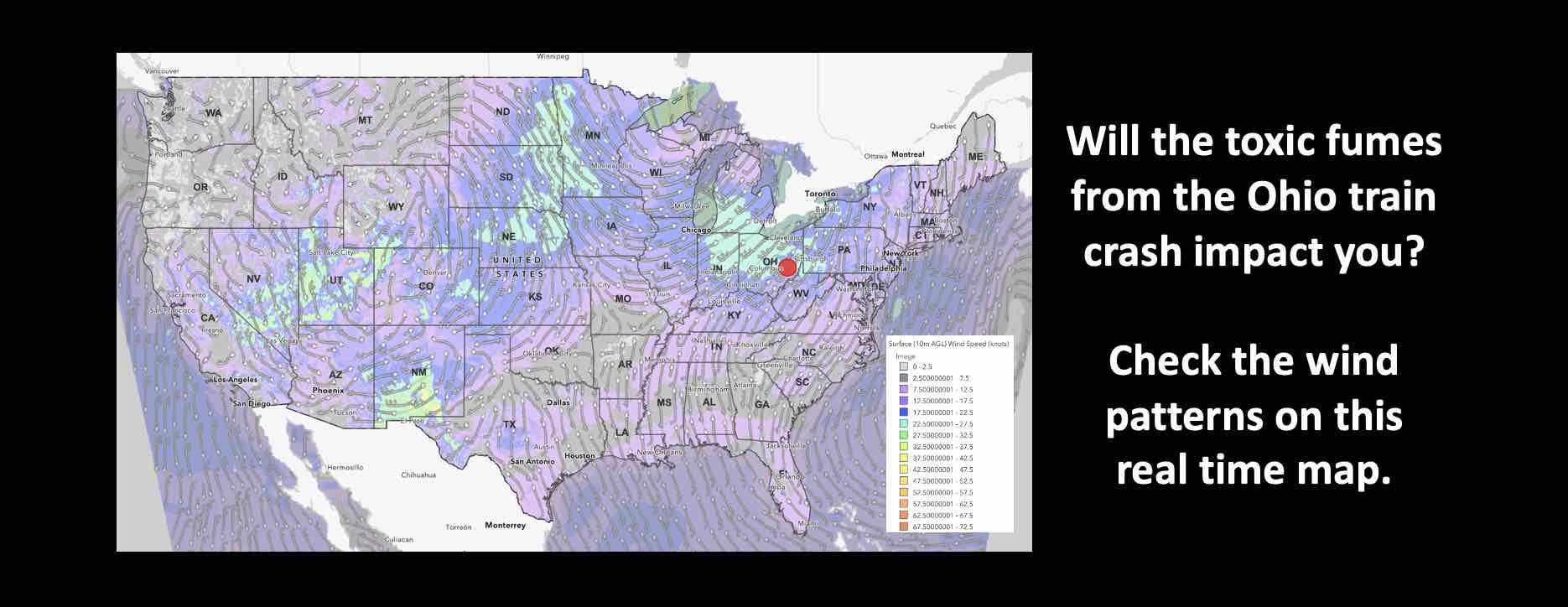 Ohio Train Derailment The Extended Impact Of Toxic Chemical Contamination On Buildings
May 05, 2025
Ohio Train Derailment The Extended Impact Of Toxic Chemical Contamination On Buildings
May 05, 2025 -
 Body Positivity And Fitness Lizzos Trainer Responds To Critics
May 05, 2025
Body Positivity And Fitness Lizzos Trainer Responds To Critics
May 05, 2025 -
 Trainer Shaun T Comments On Lizzos Alleged Ozempic Use
May 05, 2025
Trainer Shaun T Comments On Lizzos Alleged Ozempic Use
May 05, 2025 -
 National Election In Australia A Litmus Test For Global Anti Trump Sentiment
May 05, 2025
National Election In Australia A Litmus Test For Global Anti Trump Sentiment
May 05, 2025 -
 Tension On The Red Carpet Anna Kendrick And Blake Lively At Another Simple Favor
May 05, 2025
Tension On The Red Carpet Anna Kendrick And Blake Lively At Another Simple Favor
May 05, 2025
Latest Posts
-
 2025 Fox And Espn Enter The Standalone Streaming Market
May 05, 2025
2025 Fox And Espn Enter The Standalone Streaming Market
May 05, 2025 -
 Indy Car On Fox What To Expect From The Inaugural Season
May 05, 2025
Indy Car On Fox What To Expect From The Inaugural Season
May 05, 2025 -
 Fox 2 To Simulcast Red Wings And Tigers Games
May 05, 2025
Fox 2 To Simulcast Red Wings And Tigers Games
May 05, 2025 -
 Analyst Chris Fallica On Trump And Putin A Sharp Critique
May 05, 2025
Analyst Chris Fallica On Trump And Putin A Sharp Critique
May 05, 2025 -
 Nolan Speaks Out Addressing The Allegations Against Charlie Dixon
May 05, 2025
Nolan Speaks Out Addressing The Allegations Against Charlie Dixon
May 05, 2025
