High-Profile Office365 Data Breach: Millions Stolen, Hacker Charged

Table of Contents
The Scale of the Office365 Data Breach and its Impact
The sheer scale of this Office365 security breach is alarming. Initial reports suggest that upwards of five million individual and organizational accounts were compromised, resulting in the theft of a vast amount of sensitive data. The types of data stolen included:
- Emails: Millions of emails, containing confidential communications, business strategies, and personal information.
- Passwords: Compromised passwords put countless accounts across various platforms at risk, potentially leading to further data breaches and identity theft.
- Financial Information: Stolen financial data, including bank account details and credit card numbers, exposes victims to significant financial loss.
- Personal Data: The breach exposed a wealth of personal data, including addresses, phone numbers, and social security numbers, creating significant risks of identity theft and fraud.
The consequences for victims are severe and far-reaching. Identity theft, financial loss, and reputational damage are just some of the potential outcomes. The cost of data breaches is also astronomical, with organizations facing significant financial penalties, legal fees, and reputational damage. Statistics show that the average cost of a data breach continues to rise, making robust cybersecurity measures more critical than ever. This Office365 data theft underscores the escalating threat of cybercrime and the importance of proactive information security strategies.
How the Office365 Data Breach Occurred – Vulnerabilities Exploited
The hacker reportedly exploited several vulnerabilities in the Office365 system to gain unauthorized access. Their methods appear to have involved a sophisticated combination of techniques:
- Phishing Attacks: The initial infiltration likely involved highly targeted phishing emails designed to trick users into revealing their credentials. These sophisticated phishing attacks often mimic legitimate communications, making them difficult to detect.
- Malware Infection: Once access was gained, malware was likely deployed to spread laterally across the network, gaining access to more accounts and sensitive data.
- Exploitation of Weak Passwords: Many accounts were likely compromised due to the use of weak or easily guessable passwords.
A significant contributing factor appears to be the lack of multi-factor authentication (MFA) in many of the affected organizations. MFA provides an additional layer of security, significantly reducing the risk of account compromise even if passwords are stolen. Furthermore, some organizations may have lacked up-to-date security patches and regular security audits, allowing vulnerabilities to remain undetected and exploited. This Office365 vulnerabilities exposure highlights the critical need for strong password policies and multi-factor authentication.
The Arrest and Charges Against the Hacker – Legal Ramifications
Authorities have arrested a suspected hacker, identified as [insert name if available and publicly known, otherwise omit this part], located in [insert location if available and publicly known, otherwise omit this part]. They face a range of serious charges, including:
- Identity theft
- Computer fraud
- Violation of data privacy laws
The potential penalties are substantial, potentially including lengthy prison sentences and significant fines. While some data may have been recovered, the full extent of the damage may take years to fully assess. This cybersecurity prosecution sends a strong message that such crimes will not be tolerated and that the legal consequences for perpetrators are severe. This Office365 data breach highlights the importance of robust cybersecurity measures and the need for effective cybersecurity prosecution to deter future attacks.
Lessons Learned and Best Practices for Office365 Security
This Office365 data breach provides crucial lessons for organizations seeking to improve their security posture:
- Implement Multi-Factor Authentication (MFA): MFA is a crucial layer of security that significantly reduces the risk of account compromise.
- Conduct Regular Security Audits: Regular audits identify and address vulnerabilities before they can be exploited.
- Invest in Employee Cybersecurity Awareness Training: Educating employees about phishing attacks, malware, and other threats is essential.
- Enforce Strong Password Policies: Strong, unique passwords are critical for preventing unauthorized access. Consider using a password manager.
- Keep Software Updated: Regularly updating software and patching vulnerabilities is crucial for preventing attacks.
By proactively implementing these Office365 security best practices, organizations can significantly reduce their risk of experiencing a similar data breach. Resources like Microsoft's own security documentation provide detailed guidance on securing your Microsoft 365 environment.
Conclusion: Protecting Your Organization from Future Office365 Data Breaches
The high-profile Office365 data breach serves as a stark reminder of the ever-present threat of cyberattacks. The scale of the breach, the impact on victims, and the legal repercussions underscore the critical need for proactive and comprehensive security measures. Don't let your organization become the next victim of an Office365 data breach. Strengthen your security protocols today by implementing robust multi-factor authentication, conducting regular security audits, and investing in employee training. Proactive steps are vital for mitigating the risks associated with Office365 security vulnerabilities and protecting your valuable data. Review your Office365 security now and ensure your organization is adequately protected against future cyber threats.

Featured Posts
-
 Trumps Clemency Grants 26 Pardons And Commutations Including A Former Gang Leader
May 30, 2025
Trumps Clemency Grants 26 Pardons And Commutations Including A Former Gang Leader
May 30, 2025 -
 Man Uniteds Pursuit Of Sporting Star Faces Amorims Resistance
May 30, 2025
Man Uniteds Pursuit Of Sporting Star Faces Amorims Resistance
May 30, 2025 -
 Neue Liebe Neuer Sport Steffi Graf Enthuellt Details Ihrer Beziehung Zu Andre Agassi
May 30, 2025
Neue Liebe Neuer Sport Steffi Graf Enthuellt Details Ihrer Beziehung Zu Andre Agassi
May 30, 2025 -
 Trump Downplays Likelihood Of Further Russia Sanctions
May 30, 2025
Trump Downplays Likelihood Of Further Russia Sanctions
May 30, 2025 -
 M Net Firmenlauf In Augsburg Aktuelle Ergebnisse Und Fotos
May 30, 2025
M Net Firmenlauf In Augsburg Aktuelle Ergebnisse Und Fotos
May 30, 2025
Latest Posts
-
 Rebuilding After The Inferno The Texas Panhandles Post Wildfire Recovery
May 31, 2025
Rebuilding After The Inferno The Texas Panhandles Post Wildfire Recovery
May 31, 2025 -
 Out Of Control Wildfires In Eastern Manitoba A Look At The Ongoing Emergency Response
May 31, 2025
Out Of Control Wildfires In Eastern Manitoba A Look At The Ongoing Emergency Response
May 31, 2025 -
 Deadly Wildfires Continue To Threaten Eastern Manitoba Update On Firefighting Efforts
May 31, 2025
Deadly Wildfires Continue To Threaten Eastern Manitoba Update On Firefighting Efforts
May 31, 2025 -
 One Year After The Texas Panhandle Wildfire Assessing The Damage And Progress
May 31, 2025
One Year After The Texas Panhandle Wildfire Assessing The Damage And Progress
May 31, 2025 -
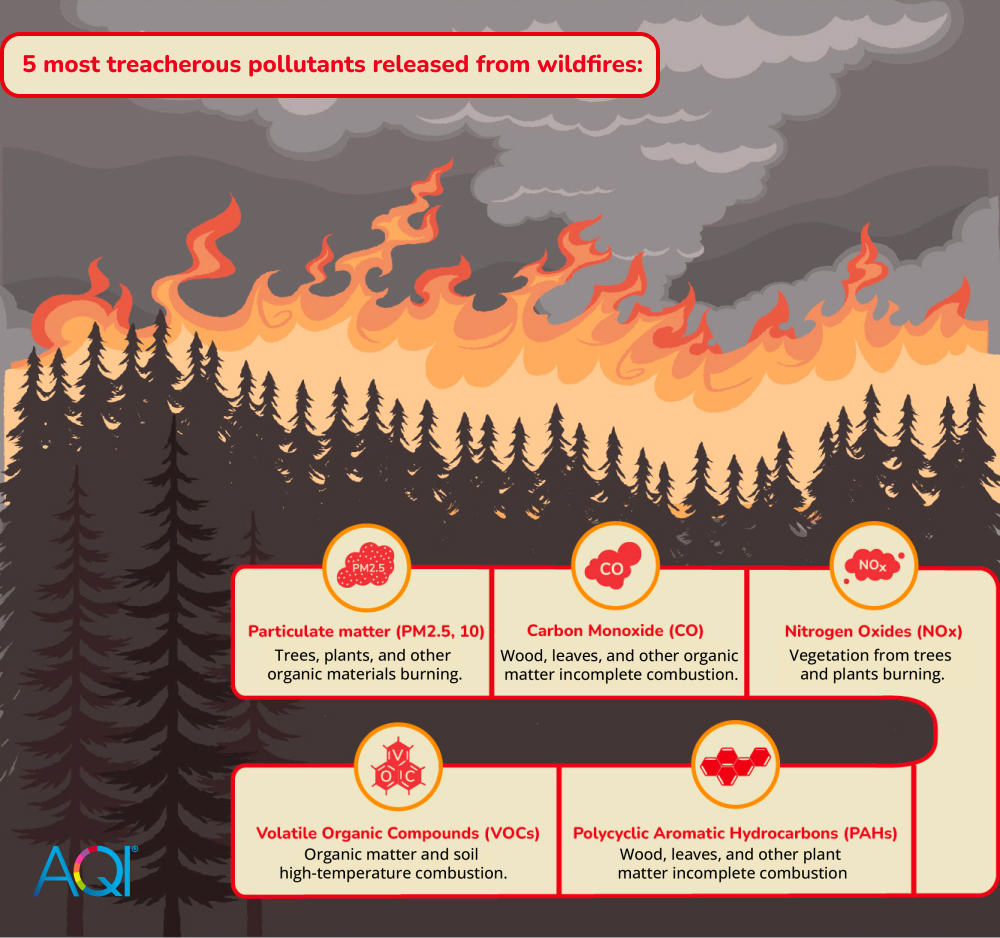 Respiratory Health Concerns Rise As Canadian Wildfires Affect Minnesota Air
May 31, 2025
Respiratory Health Concerns Rise As Canadian Wildfires Affect Minnesota Air
May 31, 2025
