Hacker's Office365 Intrusion Results In Multi-Million Dollar Loss
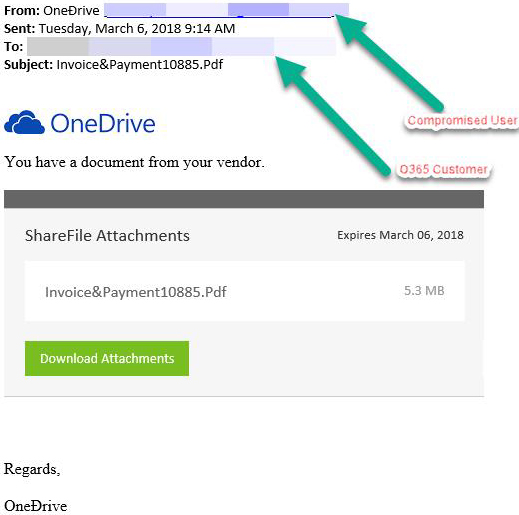
Table of Contents
The Case Study: A Detailed Look at the Office365 Breach
A medium-sized manufacturing company (anonymized for privacy) recently suffered a significant Office365 compromise, leading to a multi-million dollar loss. The hackers gained access through a sophisticated phishing attack targeting senior executives. These emails, expertly crafted to mimic legitimate communications, contained malicious attachments. Once opened, these attachments deployed malware, providing the attackers with initial access to the company's network. This Office365 data breach exposed a wide range of sensitive information.
- Initial compromise vector: A sophisticated phishing email containing a malicious macro-enabled document.
- Lateral movement within the network: The attackers leveraged compromised credentials to move laterally within the network, gaining access to various systems and applications, including the company's cloud-based storage.
- Data exfiltration methods: The hackers exfiltrated sensitive data, including customer data, financial records, and proprietary design blueprints, using a combination of techniques, such as data transfer via compromised accounts and covert data uploads to external servers.
- Ransomware deployment: After exfiltrating the data, the attackers deployed ransomware, encrypting critical files and systems, effectively halting operations. This further increased the financial burden.
This Office365 security breach exemplifies the dangers of even seemingly minor vulnerabilities. The initial phishing attack served as the catalyst for a complete network compromise, exposing the company's data and inflicting substantial financial damage.
The Financial Ramifications: Quantifying the Losses
The financial impact of this Office365 intrusion was catastrophic, totaling several million dollars. This figure encompasses both direct and indirect costs. The financial burden stemmed from multiple sources:
- Direct costs: The company incurred substantial costs related to ransom payments (though the exact amount remains undisclosed), system recovery, data restoration, and hiring specialized cybersecurity firms to remediate the attack.
- Indirect costs: The impact extends far beyond the direct financial outlay. The breach resulted in significant lost productivity due to system downtime, substantial legal fees associated with regulatory compliance and potential lawsuits, and a severe decline in customer trust, leading to lost contracts and a drop in the stock price.
The cumulative effect of these costs resulted in a substantial financial setback for the company, demonstrating the far-reaching consequences of an unchecked cyberattack. The incident serves as a stark reminder of the significant financial risk associated with inadequate cybersecurity measures.
Lessons Learned and Prevention Strategies
This case study offers critical lessons for organizations of all sizes. The vulnerabilities exploited highlight the need for comprehensive security measures, including:
- Implementing robust multi-factor authentication (MFA): MFA adds an extra layer of security, significantly hindering unauthorized access, even if credentials are compromised.
- Regular security awareness training for employees: Educating employees about phishing techniques and other social engineering tactics is crucial to mitigating the risk of successful attacks.
- Employing strong password policies: Enforcing complex passwords and regular password changes reduces the likelihood of successful brute-force or credential-stuffing attacks.
- Regular software updates and patching: Promptly applying security patches and updates to all systems and applications minimizes vulnerabilities exploited by attackers.
- Utilizing advanced threat protection solutions: Investing in advanced threat protection tools like Security Information and Event Management (SIEM) systems can help detect and respond to threats in real-time.
- Regular security audits and penetration testing: Regular assessments by security professionals can identify and address potential vulnerabilities before they can be exploited.
By implementing these Office365 security best practices, businesses can significantly reduce their risk of suffering a similar devastating Office365 intrusion.
Conclusion: Protecting Your Business from Office365 Intrusions
This case study unequivocally demonstrates the potentially devastating financial consequences of an Office365 intrusion. The hackers' methods, the extent of the data breach, and the resulting multi-million dollar losses underscore the urgency of prioritizing proactive security measures. Don't become another victim of an Office365 security breach. Implement robust security measures today to protect your valuable data and safeguard your bottom line. Investing in robust cybersecurity is not an expense; it's an investment in the future of your business. For further information on protecting your organization, consider consulting with reputable cybersecurity firms specializing in Office365 security and consider implementing regular cybersecurity awareness training for your staff.

Featured Posts
-
 Le Pens Rally A Disappointing Turnout For The National Rally In France
May 24, 2025
Le Pens Rally A Disappointing Turnout For The National Rally In France
May 24, 2025 -
 Savannah Guthries Mid Week Co Host Swap Who Filled In
May 24, 2025
Savannah Guthries Mid Week Co Host Swap Who Filled In
May 24, 2025 -
 Accentures 50 000 Promotions A Six Month Delay Explained
May 24, 2025
Accentures 50 000 Promotions A Six Month Delay Explained
May 24, 2025 -
 Planning Your Country Escape Top Tips For A Smooth Transition
May 24, 2025
Planning Your Country Escape Top Tips For A Smooth Transition
May 24, 2025 -
 Is It Ethical To Bet On The Los Angeles Wildfires Exploring The Moral Implications
May 24, 2025
Is It Ethical To Bet On The Los Angeles Wildfires Exploring The Moral Implications
May 24, 2025
Latest Posts
-
 The Stitchpossible Weekend A Look At Potential 2025 Box Office Success
May 24, 2025
The Stitchpossible Weekend A Look At Potential 2025 Box Office Success
May 24, 2025 -
 Analyzing The Stitchpossible Phenomenon 2025 Box Office Projections
May 24, 2025
Analyzing The Stitchpossible Phenomenon 2025 Box Office Projections
May 24, 2025 -
 Box Office Battle Stitchpossibles Potential For Record Breaking Weekend In 2025
May 24, 2025
Box Office Battle Stitchpossibles Potential For Record Breaking Weekend In 2025
May 24, 2025 -
 Stitchpossible Weekend Box Office 2025 Showdown Predictions
May 24, 2025
Stitchpossible Weekend Box Office 2025 Showdown Predictions
May 24, 2025 -
 Gas Prices Dip To Multi Decade Lows For Memorial Day Weekend
May 24, 2025
Gas Prices Dip To Multi Decade Lows For Memorial Day Weekend
May 24, 2025
