Federal Investigation: Hacker Made Millions Targeting Executive Office365 Accounts
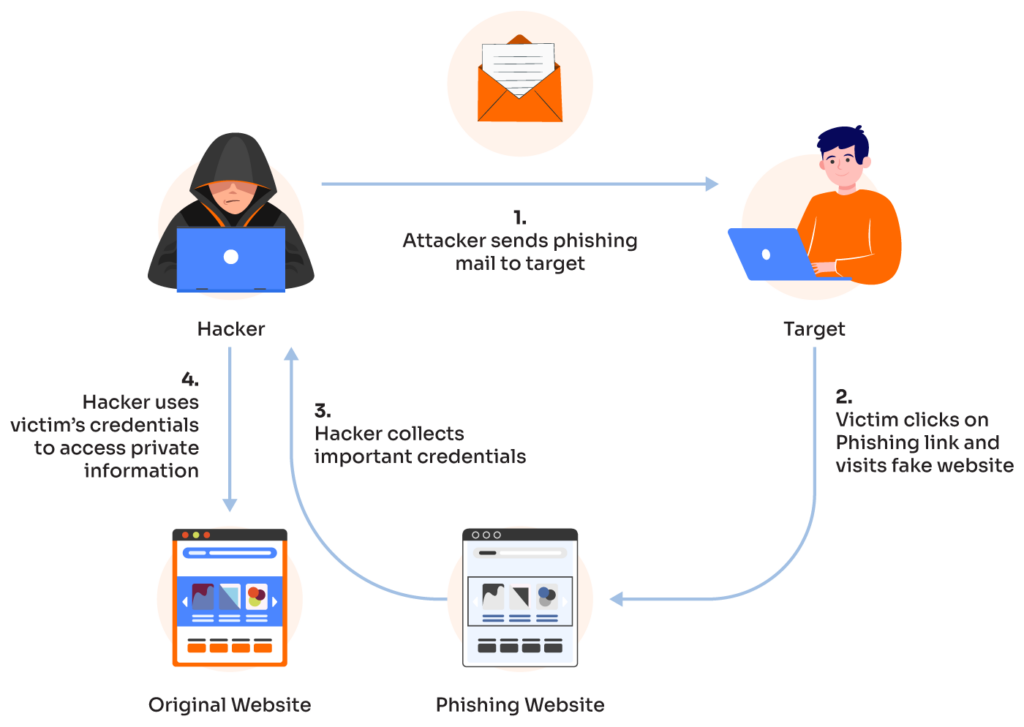
Table of Contents
The Modus Operandi of the Office365 Hack
The hackers behind this massive data breach employed a multi-pronged attack strategy, leveraging several sophisticated techniques to gain unauthorized access to executive Office365 accounts. Their modus operandi involved a combination of phishing, credential stuffing, and potentially, the deployment of sophisticated malware. They successfully bypassed standard security measures, demonstrating the need for robust and layered security protocols.
- Phishing Emails: The hackers crafted highly convincing phishing emails designed to trick executives into revealing their login credentials. These emails often mimicked legitimate communications from trusted sources, using subject lines designed to create a sense of urgency or importance.
- Example Phishing Email Subject Lines: "Urgent: Invoice Payment Required," "Action Needed: Account Security Alert," "Confidential: New Project Briefing."
- Credential Stuffing Attacks: The hackers also likely used credential stuffing, a technique where they automatically try various combinations of usernames and passwords obtained from previous data breaches against Office365 login portals. This brute-force approach can be surprisingly effective against accounts with weak or reused passwords.
- Explanation of Credential Stuffing Techniques: Hackers use automated bots to test stolen credentials against multiple online services. Success often relies on the victim reusing passwords across different platforms.
- Malware Deployment (Potential): While not confirmed, investigators suspect the hackers may have also used malware to gain persistent access to compromised accounts and systems. This malware could have enabled them to steal data discreetly over time.
- Description of Potential Malware: The type of malware deployed remains under investigation, but it likely included keyloggers or other tools capable of capturing user input and network traffic.
- Social Engineering: The hackers likely employed sophisticated social engineering techniques to manipulate individuals into divulging sensitive information or providing access to their accounts. This approach relies on human psychology rather than technical vulnerabilities.
- Examples of Social Engineering Tactics: Pretending to be IT support staff needing access to troubleshoot an account issue, or creating a false sense of urgency to pressure victims into making rash decisions. This emphasizes the need for thorough employee training.
The specific vulnerabilities exploited within the Office365 platform remain under investigation, but the case highlights the fact that no system is impenetrable. Addressing vulnerabilities, including those in third-party applications integrated with Office365, is critical.
The Scale of the Financial Losses and Data Breach
The financial losses resulting from this Office365 hack are substantial, estimated to be in the millions of dollars. The precise figure is still under investigation but involves direct financial theft and consequential damages. The breach also compromised a significant amount of sensitive data, exposing victims to serious risks.
- Estimated Financial Losses: The total financial losses are still being calculated, but early estimates suggest millions of dollars were stolen directly from accounts and lost due to fraudulent activities.
- Types of Data Compromised: The hackers accessed a variety of sensitive information, including financial records, intellectual property, client lists, and employee personal data. This breach exposed the companies involved to serious reputational and legal risks.
- Examples: Confidential financial statements, strategic plans, client contact details, employee payroll information, and more.
- Potential Consequences: The consequences of this data breach are far-reaching. Victims face the risk of identity theft, financial fraud, reputational damage, and potential legal liabilities due to regulatory non-compliance (like GDPR or CCPA violations).
The Federal Investigation and Legal Ramifications
A joint federal investigation involving the FBI and other agencies is currently underway to identify, apprehend, and prosecute the individuals responsible for this massive Office365 hack. The investigation is focused on tracing the stolen funds, identifying the perpetrators, and recovering any compromised data.
- Agencies Involved: The FBI, Secret Service, and potentially other federal and international agencies are cooperating on this complex investigation.
- Status of the Investigation: At present, the investigation is ongoing. More information, including details of arrests and indictments, is expected to emerge as the investigation progresses.
- Potential Criminal Charges and Penalties: The hackers involved face a range of serious federal charges, including wire fraud, computer fraud, and identity theft. The penalties could include lengthy prison sentences and significant fines.
Lessons Learned and Best Practices for Office365 Security
This devastating Office365 hack serves as a stark reminder of the importance of robust cybersecurity measures. Organizations must prioritize security best practices to protect their sensitive data and prevent similar attacks.
- Multi-Factor Authentication (MFA): Implementing MFA is crucial to add an extra layer of security beyond simple passwords. It requires users to verify their identity through a second factor (e.g., a code sent to their phone).
- Strong Password Policies: Enforcing strong, unique passwords for each account is vital. Password managers can help users create and manage complex passwords effectively.
- Security Awareness Training: Regular security awareness training for employees is essential to educate them about phishing scams, social engineering tactics, and other potential threats.
- Data Encryption: Encrypting sensitive data both in transit and at rest provides an additional layer of protection, even if a breach occurs.
- Regular Security Audits: Regular security audits and penetration testing can identify and address vulnerabilities in systems and processes before they can be exploited by hackers.
- Threat Detection and Incident Response Planning: A robust threat detection system, combined with a well-defined incident response plan, is critical for minimizing the damage caused by a successful cyberattack.
Conclusion:
The federal investigation into the massive Office365 hack targeting executive accounts underscores the critical need for robust cybersecurity measures. Millions of dollars were lost and sensitive data compromised, highlighting the devastating consequences of neglecting digital security. This case demonstrates that even sophisticated systems can be vulnerable to determined attackers, emphasizing the need for a multi-layered approach to cybersecurity. Don't become another victim. Strengthen your Office365 security today by implementing strong authentication, regular security audits, and comprehensive employee training. Protect your executive accounts and your bottom line from costly Office365 hacks. Investing in proactive security measures is not an expense—it's an investment in the long-term health and success of your organization.

Featured Posts
-
 Is Colapinto The Next Red Bull Driver Lawsons Position Under Scrutiny
May 09, 2025
Is Colapinto The Next Red Bull Driver Lawsons Position Under Scrutiny
May 09, 2025 -
 108 000 Funding Injection For Madeleine Mc Cann Case
May 09, 2025
108 000 Funding Injection For Madeleine Mc Cann Case
May 09, 2025 -
 Nome Bound Meet The 7 Rookie Iditarod Mushers
May 09, 2025
Nome Bound Meet The 7 Rookie Iditarod Mushers
May 09, 2025 -
 One Cryptocurrency Surviving The Trade War Fallout
May 09, 2025
One Cryptocurrency Surviving The Trade War Fallout
May 09, 2025 -
 The Ultimate Stephen King Reading List 5 Books You Cant Miss
May 09, 2025
The Ultimate Stephen King Reading List 5 Books You Cant Miss
May 09, 2025
