FBI Investigation: Large-Scale Office365 Data Breach And Theft

Table of Contents
The Scale and Impact of the Office365 Data Breach
The sheer scale of this Office365 data breach is staggering. While the exact numbers of affected users and organizations remain under investigation by the FBI, early reports suggest thousands of accounts across various industries were compromised. The stolen data encompasses sensitive information, including customer databases, financial records, intellectual property, and employee personal details. The potential consequences are far-reaching and devastating.
- Compromised Data Examples: The breach reportedly exposed personally identifiable information (PII), including names, addresses, social security numbers, and credit card details. Intellectual property theft is also a significant concern, potentially leading to competitive disadvantages and financial losses for affected companies.
- Financial and Reputational Damage: The financial repercussions can be immense, involving costs associated with remediation, legal fees, regulatory fines, and potential loss of business. Reputational damage can be equally crippling, impacting customer trust and brand loyalty. A damaged reputation can take years to rebuild.
- Long-Term Consequences: Beyond immediate financial losses, individuals affected by the Office365 data breach face the risk of identity theft and financial fraud. Organizations may experience long-term impacts on their operations, including decreased productivity and strained relationships with clients and partners. The lasting impact of a data breach can significantly impact an organization's bottom line and overall success.
Methods Used in the Office365 Data Breach
The attackers leveraged a sophisticated combination of techniques to gain unauthorized access to Office365 accounts. Preliminary findings suggest a multi-pronged approach, combining social engineering with advanced malware and exploiting vulnerabilities in third-party applications.
- Phishing Attacks: Spear phishing and whaling attacks, targeting specific high-value individuals within organizations, were likely employed to obtain initial access credentials. These highly targeted attacks often use deceptive emails or websites to trick users into revealing sensitive information.
- Malware and Credential Stuffing: Once initial access is gained, malware is frequently used to escalate privileges and steal further data. Credential stuffing, where attackers use stolen usernames and passwords from other data breaches to access accounts, also plays a significant role.
- Compromised Third-Party Applications: Attackers often exploit vulnerabilities in less secure third-party applications integrated with Office365. This allows them to bypass the inherent security of Office365 itself, gaining access through a less protected entry point.
The FBI's Response and Investigation into the Office365 Data Breach
The FBI is actively investigating this large-scale Office365 data breach, collaborating with international law enforcement agencies and cybersecurity experts. The investigation aims to identify the perpetrators, understand the full extent of the damage, and bring those responsible to justice.
- FBI Investigation Process: The investigation involves analyzing the compromised systems, tracing the attackers' activities, and identifying potential vulnerabilities exploited in the breach. This comprehensive approach is designed to uncover the full scope of the attack and prevent future incidents.
- Public Statements and Warnings: The FBI has issued public warnings about the increasing sophistication of cyberattacks targeting Office365 and similar cloud-based services. They urge organizations to adopt proactive security measures to protect their data and systems.
- Collaborative Efforts: The FBI's investigation benefits from collaboration with other law enforcement agencies, both domestically and internationally, allowing for a coordinated and effective response to transnational cybercrime.
Protecting Your Organization from Office365 Data Breaches
The best defense against an Office365 data breach is a multi-layered security approach. Proactive measures are crucial to mitigate risk and protect your organization's valuable data.
- Multi-Factor Authentication (MFA): Implementing MFA is paramount. This adds an extra layer of security, requiring users to provide multiple forms of authentication to access their accounts, significantly reducing the risk of unauthorized access even if passwords are compromised.
- Strong Password Policies and Password Management: Enforce strong password policies, requiring complex and regularly changed passwords. Utilize password management tools to securely store and manage credentials.
- Regular Software Updates and Vulnerability Patching: Regularly update software and operating systems to patch known vulnerabilities. This prevents attackers from exploiting known weaknesses to gain access to your systems.
- Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify and address vulnerabilities before attackers can exploit them. This proactive approach helps identify and mitigate weaknesses in your security posture.
- Employee Security Awareness Training: Educate employees about phishing and social engineering tactics to prevent them from becoming victims of attacks. Regular training is essential to ensure employees remain vigilant against sophisticated attacks.
- Advanced Threat Protection and Data Loss Prevention (DLP): Utilize Office365's advanced threat protection features and implement DLP measures to monitor and prevent sensitive data from leaving your organization's control.
Conclusion
The FBI investigation into this large-scale Office365 data breach serves as a stark reminder of the ever-present threat of cyberattacks. The scale and impact of this breach highlight the critical need for robust security measures to protect against data theft and financial loss. The consequences of an Office365 data breach extend far beyond immediate financial losses; they can include reputational damage, legal liabilities, and long-term operational disruptions. By proactively implementing the security measures outlined above, your organization can significantly reduce its vulnerability to similar Office365 data breaches and protect its valuable assets. Take action today. Review and strengthen your Office365 security protocols now to minimize your risk. For further information on best practices for Office365 security, consult resources like [link to relevant resource 1] and [link to relevant resource 2].

Featured Posts
-
 Florida Film Festival 2024 Celebrity Sightings Mia Farrow And Christina Ricci
May 24, 2025
Florida Film Festival 2024 Celebrity Sightings Mia Farrow And Christina Ricci
May 24, 2025 -
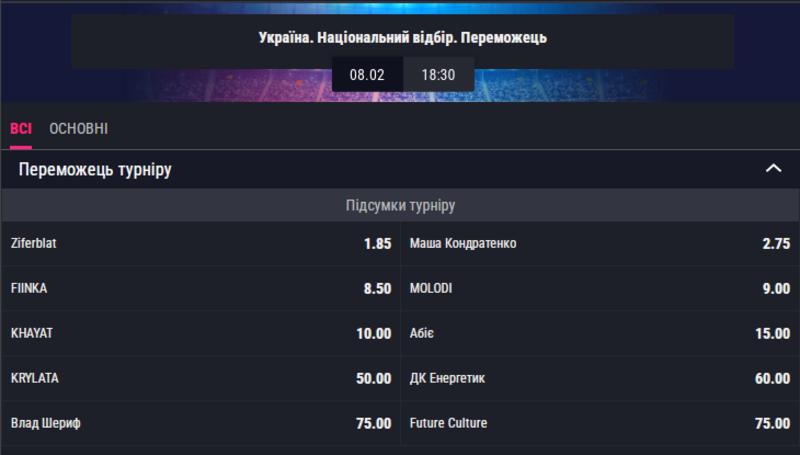 Prognoz Konchiti Vurst Peremozhtsi Yevrobachennya 2025
May 24, 2025
Prognoz Konchiti Vurst Peremozhtsi Yevrobachennya 2025
May 24, 2025 -
 A Comprehensive Look At The Countrys Top Business Locations
May 24, 2025
A Comprehensive Look At The Countrys Top Business Locations
May 24, 2025 -
 The Sean Penn Story A Look At His Recent Claims And Public Reaction
May 24, 2025
The Sean Penn Story A Look At His Recent Claims And Public Reaction
May 24, 2025 -
 France Political Push To Ban Hijabs For Girls Under 15 Years Old
May 24, 2025
France Political Push To Ban Hijabs For Girls Under 15 Years Old
May 24, 2025
Latest Posts
-
 Record Low Gas Prices Predicted For Memorial Day Weekend
May 24, 2025
Record Low Gas Prices Predicted For Memorial Day Weekend
May 24, 2025 -
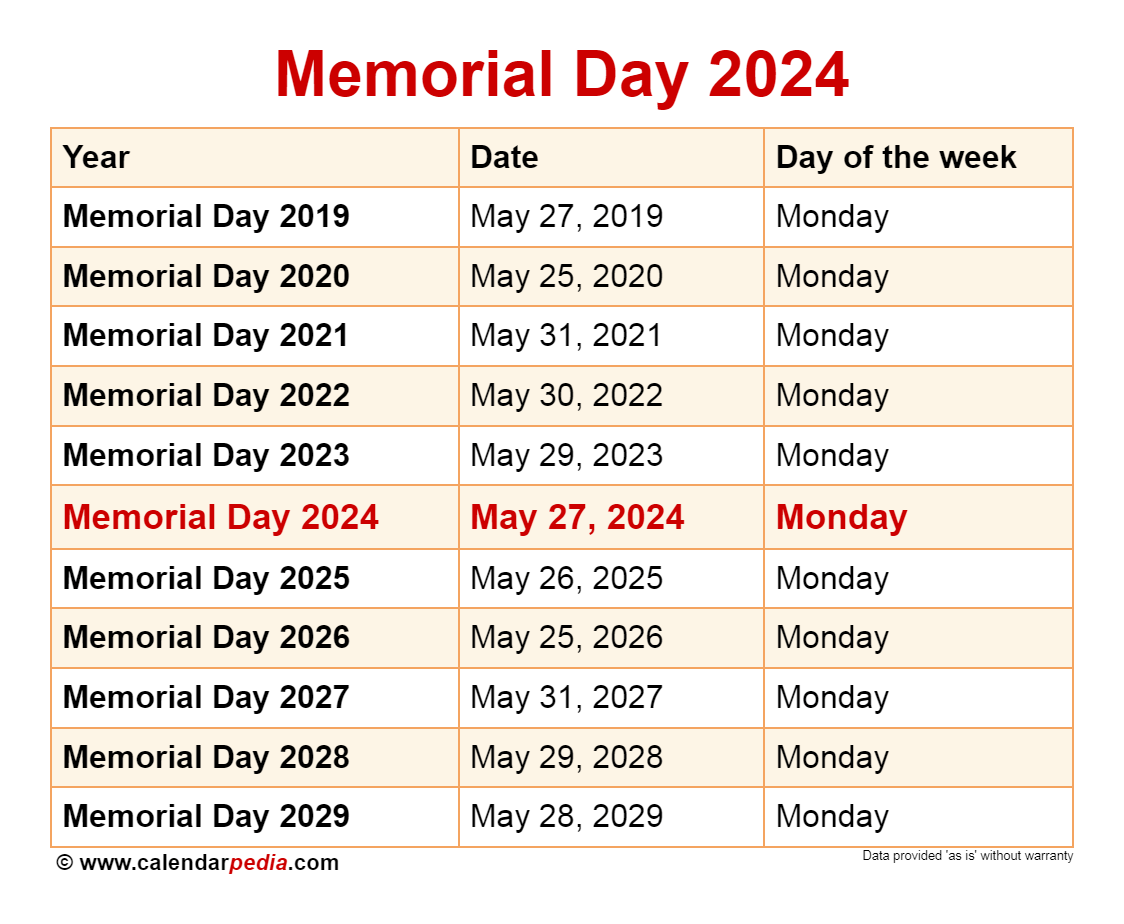 Sandy Point Rehoboth Ocean City Beaches Memorial Day Weekend 2025 Weather Prediction
May 24, 2025
Sandy Point Rehoboth Ocean City Beaches Memorial Day Weekend 2025 Weather Prediction
May 24, 2025 -
 2025 Memorial Day Weekend Beach Forecast Ocean City Rehoboth Sandy Point
May 24, 2025
2025 Memorial Day Weekend Beach Forecast Ocean City Rehoboth Sandy Point
May 24, 2025 -
 Ocean City Rehoboth Sandy Point Beach Weather Memorial Day Weekend 2025 Forecast
May 24, 2025
Ocean City Rehoboth Sandy Point Beach Weather Memorial Day Weekend 2025 Forecast
May 24, 2025 -
 Celebrated Amphibian Speaker At University Of Maryland Commencement Ceremony
May 24, 2025
Celebrated Amphibian Speaker At University Of Maryland Commencement Ceremony
May 24, 2025
