Executive Office365 Accounts Targeted In Multi-Million Dollar Cybercrime Ring
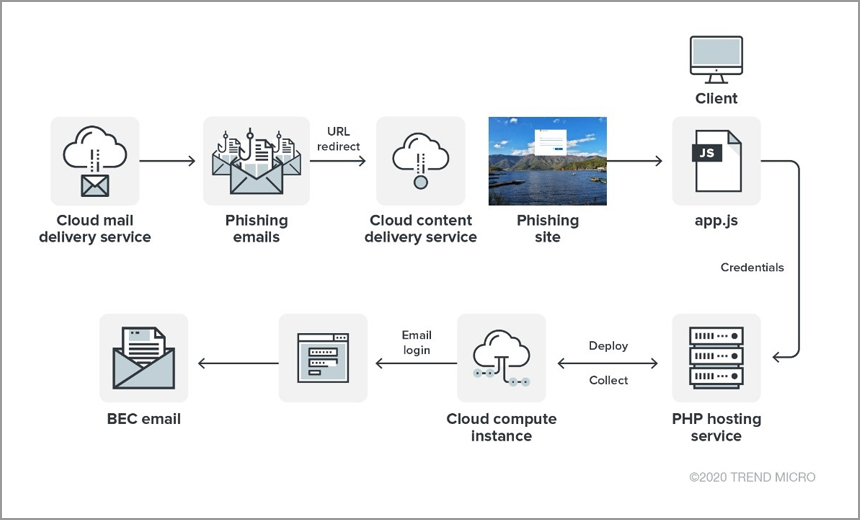
Table of Contents
The Sophistication of the Cybercrime Ring Targeting Executive Office365 Accounts
This multi-million dollar cybercrime ring demonstrated a level of sophistication rarely seen in typical phishing campaigns. Their success hinged on a combination of advanced techniques, exploiting vulnerabilities in both technology and human behavior.
Advanced Phishing Techniques Employed
The criminals employed a range of advanced phishing techniques, focusing their efforts on high-value targets: executive Office365 accounts. These included:
- Spear Phishing: Highly targeted emails crafted to appear legitimate, often containing specific details about the target's company or personal information. These emails often mimicked internal communications or requests from trusted sources.
- CEO Fraud (or Business Email Compromise - BEC): These attacks impersonate senior executives to trick employees into transferring funds or revealing sensitive information. The criminals often used convincing email addresses and forged signatures to increase their credibility.
- Whaling: A particularly aggressive form of spear phishing that targets high-profile individuals, such as CEOs, CFOs, and other executives, directly. These attacks often involved extensive research to personalize the phishing attempts.
The attackers also leveraged sophisticated malware, including custom-built tools designed to bypass security measures and exfiltrate data discreetly. While specific malware used in this particular ring remains undisclosed for investigative reasons, the use of such tools is a common characteristic of these advanced attacks.
Exploiting Weaknesses in Multi-Factor Authentication (MFA)
Despite the widespread adoption of Multi-Factor Authentication (MFA), the criminals found ways to circumvent these security measures. This highlights the critical need for robust MFA implementation and ongoing awareness training. Methods used included:
- SIM Swapping: The criminals illegally obtained control of the target's mobile phone number, allowing them to intercept MFA codes sent via SMS.
- Phishing for MFA Codes: Tricking users into revealing their MFA codes through cleverly disguised phishing emails or websites.
- Exploiting Weak MFA Implementations: Targeting organizations with weak or improperly configured MFA systems.
Data Breaches and Exfiltration Methods
Once access to Executive Office365 accounts was gained, the criminals exfiltrated a range of sensitive data, including:
- Financial Records: Bank account details, transaction histories, and investment information.
- Intellectual Property: Confidential documents, designs, and trade secrets.
- Confidential Communications: Internal emails, strategic plans, and sensitive negotiations.
Data exfiltration methods included the use of cloud storage services and compromised email accounts to transfer stolen data outside the organization's network. The scale and speed of data exfiltration underscore the urgent need for robust data loss prevention (DLP) measures.
The Financial Impact of the Multi-Million Dollar Cybercrime Ring
The financial impact of this cybercrime ring was substantial, extending far beyond the immediate theft of funds.
Estimating the Total Losses
The total losses, estimated at several million dollars, comprised both direct financial losses and indirect costs. The direct losses included stolen funds transferred through compromised bank accounts and fraudulent payments.
Types of Financial Losses
The financial losses were multifaceted:
- Direct Financial Theft: Funds directly stolen from company accounts.
- Loss of Intellectual Property: The cost of lost competitive advantage and potential future revenue.
- Legal Fees: Expenses incurred in investigating the breach, notifying affected parties, and dealing with regulatory issues.
- Reputational Damage: The loss of customer trust and potential impact on investor confidence.
The Ripple Effect on Businesses and Investors
Attacks targeting Executive Office365 accounts have a ripple effect. The loss of sensitive data can lead to decreased investor confidence, impacting stock prices and making it harder to secure funding. Furthermore, the reputational damage can affect future business relationships and customer loyalty.
Protecting Executive Office365 Accounts from Similar Attacks
Protecting your Executive Office365 accounts requires a multi-layered approach encompassing technology, processes, and employee training.
Strengthening Password Security
Strong passwords are fundamental. Encourage the use of complex, unique passwords for each account and utilize a reputable password manager to securely store and manage these credentials. Implement password policies that enforce complexity and regular changes.
Implementing Robust MFA
Deploy strong MFA across all Executive Office365 accounts. Consider using authenticator apps, hardware tokens, or other methods beyond simple SMS-based verification to significantly enhance security. Regularly review and update your MFA settings to adapt to evolving threats.
Regular Security Training and Awareness
Invest in ongoing security awareness training for all employees, particularly executives. Regular phishing simulations and training sessions can help employees identify and avoid phishing attempts. Emphasis should be placed on recognizing suspicious emails, websites, and communications.
Leveraging Advanced Security Solutions
Consider implementing advanced security solutions like:
- Threat Intelligence: Stay informed about emerging threats and vulnerabilities.
- Intrusion Detection Systems (IDS): Monitor network traffic for suspicious activity.
- Email Security Solutions: Implement advanced email filtering and anti-phishing capabilities.
Conclusion
This multi-million dollar cybercrime ring targeting Executive Office365 accounts underscores the growing sophistication and financial impact of cyberattacks. The criminals used advanced techniques to exploit vulnerabilities in both technology and human behavior, resulting in significant financial losses and reputational damage. By prioritizing robust password security, implementing strong MFA, conducting regular security training, and leveraging advanced security solutions, organizations can significantly reduce their risk and protect their Executive Office365 accounts from similar attacks. Don't become the next victim of a multi-million dollar Office365 cyberattack – take action now! Protect your Executive Office365 accounts today!

Featured Posts
-
 Washington Dc 2025 Unveiling The 500 Most Influential Figures
May 11, 2025
Washington Dc 2025 Unveiling The 500 Most Influential Figures
May 11, 2025 -
 Manon Fiorot The Rising French Star Of The Ufc
May 11, 2025
Manon Fiorot The Rising French Star Of The Ufc
May 11, 2025 -
 The Truth Behind Jessica Simpsons Snake Sperm Comments
May 11, 2025
The Truth Behind Jessica Simpsons Snake Sperm Comments
May 11, 2025 -
 The Medieval Tale Of Merlin And Arthur A Book Covers Hidden Depths
May 11, 2025
The Medieval Tale Of Merlin And Arthur A Book Covers Hidden Depths
May 11, 2025 -
 The Henry Cavill Nova Rumor A Deep Dive Into The Speculation
May 11, 2025
The Henry Cavill Nova Rumor A Deep Dive Into The Speculation
May 11, 2025
