Executive Email Compromise: Millions Lost In Office365 Data Breach
Table of Contents
Understanding Executive Email Compromise (EEC) Attacks
How EEC Attacks Work
Executive Email Compromise (EEC) attacks are highly targeted phishing campaigns designed to trick executives into performing actions that compromise company finances. Attackers meticulously research their victims, studying their communication patterns and relationships to craft incredibly convincing phishing emails. Here's how a typical EEC attack unfolds:
- Targeting High-Level Executives: Attackers focus on individuals with significant financial authority, knowing a successful compromise can yield maximum financial gain.
- Crafting Convincing Phishing Emails: Emails often mimic legitimate communications, such as invoices, payment requests, or urgent business correspondence, to bypass suspicion. They may even include forged signatures or logos.
- Exploiting Trust Relationships: Attackers often leverage existing relationships, pretending to be a trusted colleague, vendor, or client to increase the likelihood of success.
- Gaining Access to Financial Systems: Once the initial compromise is achieved (often through a malicious link or attachment), attackers seek access to financial systems to initiate fraudulent transactions. This may involve stealing login credentials or deploying malware.
The Office365 Vulnerability
Despite its robust security features, Office365 remains a prime target for EEC attacks. Attackers exploit vulnerabilities such as:
- Compromised Credentials: Weak passwords, password reuse, and a lack of multi-factor authentication (MFA) make it easier for attackers to gain unauthorized access.
- Successful Phishing Campaigns Bypassing MFA: Even with MFA enabled, sophisticated phishing tactics can still trick victims into revealing authentication codes.
- Exploiting Application Vulnerabilities: Attackers actively seek and exploit vulnerabilities within Office365 applications and integrations.
The Financial Ramifications of Office365 Data Breaches
Direct Financial Losses
The direct financial consequences of successful EEC attacks can be catastrophic. These include:
- Wire Transfer Fraud: Attackers often redirect funds to offshore accounts through fraudulent wire transfers. Losses can range from tens of thousands to millions of dollars.
- Invoice Redirection: Attackers intercept legitimate invoices, altering payment instructions to redirect funds to their own accounts.
- Data Extortion: Attackers may exfiltrate sensitive data and demand a ransom for its return or to prevent its public release.
Indirect Costs
Beyond the direct financial losses, EEC attacks trigger significant indirect costs, including:
- Legal Fees: Investigating the breach, notifying affected parties, and dealing with potential legal action can be extremely costly.
- Reputational Damage: A successful EEC attack can severely damage a company's reputation, leading to loss of customer trust and future business opportunities.
- Loss of Customer Trust: Customers may be hesitant to do business with a company that has experienced a data breach, impacting future revenue.
- Operational Disruptions: Responding to a data breach requires significant resources and time, disrupting normal business operations.
Protecting Your Organization from Executive Email Compromise
Implementing Robust Security Measures
Proactive security measures are crucial in mitigating the risk of EEC attacks. These include:
- Enforce Strong Password Policies and MFA: Implement robust password policies and mandatory multi-factor authentication (MFA) to enhance account security.
- Deploy Email Security Solutions (Anti-phishing, Anti-malware): Invest in advanced email security solutions that can detect and block phishing attempts and malicious attachments.
- Conduct Regular Employee Security Awareness Training: Educate employees about phishing techniques, social engineering tactics, and the importance of secure email practices.
- Implement Robust Access Controls: Limit access to sensitive financial systems and data to authorized personnel only.
The Role of Employee Training
Employee training is paramount in preventing EEC attacks. Regular security awareness training should cover:
- Identifying Phishing Emails: Teach employees how to spot suspicious emails, including inconsistencies in grammar, sender addresses, and urgent requests for immediate action.
- Verifying Requests: Encourage employees to independently verify requests for funds or sensitive information before acting on them.
- Reporting Suspicious Activity: Establish clear reporting procedures for suspicious emails or activity.
Case Studies of Successful EEC Attacks
Numerous high-profile cases demonstrate the devastating impact of EEC attacks. [Insert links to relevant news articles or reports here, showcasing successful EEC attacks against Office365 users.] These real-world examples highlight the urgent need for robust security measures and continuous employee training.
Conclusion
Executive Email Compromise attacks targeting Office365 users pose a significant threat to businesses of all sizes, resulting in substantial financial losses and reputational damage. The vulnerabilities within Office365, coupled with sophisticated phishing techniques, highlight the need for a multi-layered approach to cybersecurity. By implementing strong password policies, multi-factor authentication, advanced email security solutions, and comprehensive employee training, organizations can significantly reduce their risk of falling victim to EEC attacks. Don't become another victim of Executive Email Compromise. Invest in comprehensive email security and employee training today! [Insert links to relevant resources here, such as cybersecurity solutions or training providers.]

Featured Posts
-
 Sheins London Ipo Delay Impact Of Us Tariffs
May 04, 2025
Sheins London Ipo Delay Impact Of Us Tariffs
May 04, 2025 -
 Blake Lively And Anna Kendrick Reunite Putting Feud Rumors To Rest At Premiere
May 04, 2025
Blake Lively And Anna Kendrick Reunite Putting Feud Rumors To Rest At Premiere
May 04, 2025 -
 What Happened At That Wild Crypto Party A Two Day Recap
May 04, 2025
What Happened At That Wild Crypto Party A Two Day Recap
May 04, 2025 -
 How Much Do Lizzo Concert Tickets Cost A Guide To Pricing
May 04, 2025
How Much Do Lizzo Concert Tickets Cost A Guide To Pricing
May 04, 2025 -
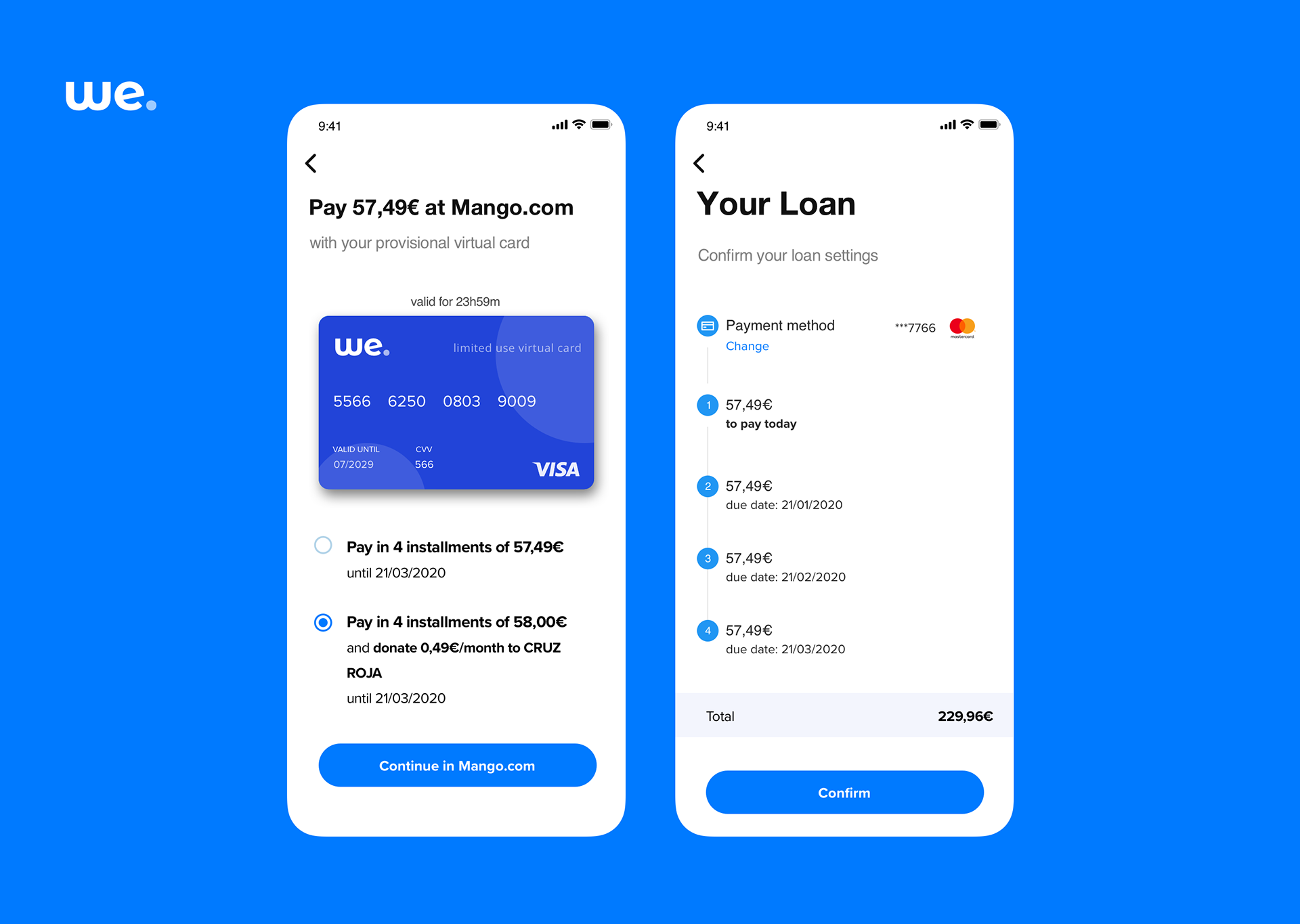 Enhanced Payment Flexibility On Spotifys I Phone App
May 04, 2025
Enhanced Payment Flexibility On Spotifys I Phone App
May 04, 2025
Latest Posts
-
 Paddy Pimblett And Dustin Poirier Retirement And The Future Of Ufc
May 04, 2025
Paddy Pimblett And Dustin Poirier Retirement And The Future Of Ufc
May 04, 2025 -
 Ufc 314 Complete Fight Card Date And Where To Watch
May 04, 2025
Ufc 314 Complete Fight Card Date And Where To Watch
May 04, 2025 -
 Paddy Pimblett On Dustin Poiriers Retirement A Critical Analysis
May 04, 2025
Paddy Pimblett On Dustin Poiriers Retirement A Critical Analysis
May 04, 2025 -
 Paddy Pimblett Was Dustin Poirier Wrong To Retire
May 04, 2025
Paddy Pimblett Was Dustin Poirier Wrong To Retire
May 04, 2025 -
 Did Jean Silva Curse At Bryce Mitchell Ufc 314 Press Conference Fallout
May 04, 2025
Did Jean Silva Curse At Bryce Mitchell Ufc 314 Press Conference Fallout
May 04, 2025
