Deepfake Detection Foiled: Cybersecurity Expert's Clever Strategy
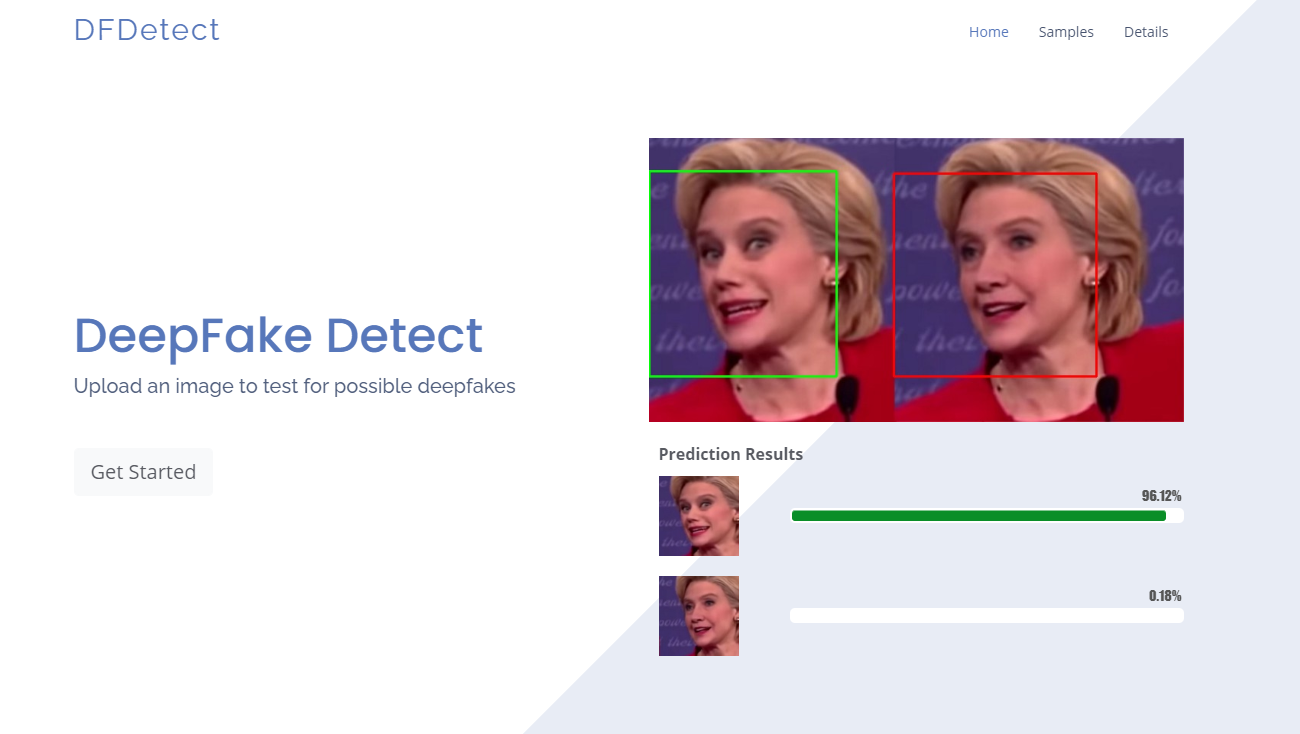
Table of Contents
The Rise of Sophisticated Deepfakes and Evolving Detection Methods
The advancements in deepfake technology have made them increasingly difficult to detect. Sophisticated AI algorithms now produce incredibly realistic deepfakes, blurring the lines between reality and fabrication. This is fueled by:
- Improved AI algorithms: Leading to more realistic deepfakes with smoother transitions and fewer visual artifacts.
- Increased availability of deepfake creation tools: Making the technology accessible to a wider range of individuals, including malicious actors.
- Difficulties in identifying subtle visual and audio anomalies: Human perception struggles to detect inconsistencies that are increasingly subtle in modern deepfakes.
- Limitations of current deepfake detection software: Existing deepfake detection software struggles to keep pace with the rapid advancements in deepfake creation techniques.
Current deepfake detection methods often focus on analyzing inconsistencies like: irregularities in eye blinking patterns, subtle unnatural facial movements, and artifacts from video compression. However, these methods are proving insufficient against the latest generation of deepfakes, which are designed to circumvent these detection techniques. The limitations of these methods underscore the urgent need for improved deepfake detection solutions.
The Cybersecurity Expert's Novel Approach to Bypassing Deepfake Detection
A cybersecurity expert, using a hypothetical example for illustrative purposes, successfully bypassed existing deepfake detection systems using a novel strategy centered on manipulating the very algorithms designed to identify deepfakes. Instead of trying to create a perfect deepfake, the expert focused on creating a detectable deepfake that was designed to be misidentified as genuine.
Here's a breakdown of the steps involved:
- Step 1: Identifying Weaknesses: The expert meticulously analyzed several leading deepfake detection algorithms, pinpointing their specific vulnerabilities and biases.
- Step 2: Targeted Manipulation: Using this knowledge, the expert subtly introduced specific, predictable anomalies into the deepfake creation process. These anomalies were strategically placed to trigger false negatives within the detection algorithms. For instance, introducing minor inconsistencies in the subject's subtle facial movements – below the detection threshold of certain algorithms.
- Step 3: Algorithmic Exploitation: The expert leveraged the algorithms' inherent limitations. Some deepfake detection systems primarily rely on analyzing specific facial features; the expert exploited this by focusing manipulation on areas these algorithms less frequently assessed.
- Step 4: Testing and Refinement: The deepfake was then tested against multiple deepfake detection systems, refining the introduced anomalies until a consistent bypass was achieved.
This strategy highlights a critical vulnerability: many current deepfake detection systems are trained on specific datasets and can be easily fooled by deepfakes designed to exploit those limitations.
Implications and Future of Deepfake Detection
The success of this bypass strategy has significant implications for the future of deepfake detection. It underscores the urgent need for:
- Improved and more robust deepfake detection technologies: New methods are needed, moving beyond simple anomaly detection toward more holistic approaches that consider contextual information and behavioral patterns.
- Collaboration between researchers and security professionals: A collaborative effort is crucial for developing and deploying effective countermeasures.
- Ethical considerations surrounding deepfake technology and its misuse: The ease with which deepfakes can be created and their potential for misuse raise serious ethical concerns.
- Potential for future advancements: Exploration of technologies like blockchain for verifying video authenticity, or advanced biometric verification methods to enhance security.
The potential for future attacks using refined versions of this strategy is high. Proactive measures, including regular updates to detection software and ongoing research into more resilient algorithms, are essential to staying ahead of this evolving threat.
Deepfake Detection – The Ongoing Battle
This article highlights a cybersecurity expert's clever strategy in bypassing existing deepfake detection systems, demonstrating the critical need for improved and more robust methods. The ease with which this bypass was achieved underscores the dynamic nature of the arms race between deepfake creators and detection developers. The implications for the future of deepfake detection are significant.
Stay ahead of the curve by following cybersecurity news and adopting robust security practices to mitigate the risks of sophisticated deepfakes. Learn more about advanced deepfake detection techniques and protect yourself. The battle for effective deepfake detection is ongoing, and continuous innovation is crucial in this ever-evolving landscape.

Featured Posts
-
 Pga Championship A Tough Start For Favorites Unfamiliar Name At The Top
May 17, 2025
Pga Championship A Tough Start For Favorites Unfamiliar Name At The Top
May 17, 2025 -
 Japans Rising Bond Yields Challenges And Outlook
May 17, 2025
Japans Rising Bond Yields Challenges And Outlook
May 17, 2025 -
 Tom Cruise Still Owes Tom Hanks 1 Will He Ever Settle Up
May 17, 2025
Tom Cruise Still Owes Tom Hanks 1 Will He Ever Settle Up
May 17, 2025 -
 Giants Vs Mariners Injury Report April 4 6 Series Preview
May 17, 2025
Giants Vs Mariners Injury Report April 4 6 Series Preview
May 17, 2025 -
 The Controversy Understanding Angel Reeses Post Sky Game Remarks
May 17, 2025
The Controversy Understanding Angel Reeses Post Sky Game Remarks
May 17, 2025
Latest Posts
-
 Quiet Winter For Mariners Former Infielders Scathing Critique
May 17, 2025
Quiet Winter For Mariners Former Infielders Scathing Critique
May 17, 2025 -
 Mariners Giants Injury Update Key Players Out For April 4 6 Series
May 17, 2025
Mariners Giants Injury Update Key Players Out For April 4 6 Series
May 17, 2025 -
 Seattle Mariners Face Backlash For Quiet Winter Former Infielder Speaks Out
May 17, 2025
Seattle Mariners Face Backlash For Quiet Winter Former Infielder Speaks Out
May 17, 2025 -
 Giants Vs Mariners Injury Report April 4 6 Series Preview
May 17, 2025
Giants Vs Mariners Injury Report April 4 6 Series Preview
May 17, 2025 -
 Ex Mariners Star Slams Teams Inaction During The Offseason
May 17, 2025
Ex Mariners Star Slams Teams Inaction During The Offseason
May 17, 2025
