Data Center Security Breach: Deutsche Bank Contractor And Unauthorized Access

Table of Contents
The Scale and Scope of the Deutsche Bank Data Center Breach
The full extent of the Deutsche Bank data center security breach is still emerging, but initial reports paint a concerning picture. While precise figures regarding the amount of data compromised remain undisclosed, the incident involved unauthorized access to critical systems. The breach triggered a comprehensive data breach investigation, classifying it as a serious cybersecurity incident with potentially far-reaching implications. The vulnerability allowed the unauthorized party to access sensitive information, potentially including customer data, financial records, and internal documents. The geographical impact is also significant, as Deutsche Bank operates globally, meaning the consequences could extend far beyond a single location.
- Number of affected systems: The exact number remains confidential, but early assessments suggest a significant portion of the bank's infrastructure was affected.
- Types of data compromised: This potentially includes sensitive customer financial data (account numbers, balances, transaction history), personally identifiable information (PII), and internal documents containing confidential business strategies.
- Geographic impact of the breach: The breach likely impacted data centers and systems across multiple geographical regions where Deutsche Bank operates, potentially affecting customers and operations worldwide. This underscores the global nature of cybersecurity threats and the need for comprehensive, internationally compliant security measures.
The Role of the Contractor in the Data Center Security Breach
The involvement of a contractor adds a disturbing dimension to this data center security breach. The contractor's responsibilities within Deutsche Bank's infrastructure are yet to be fully disclosed, but their access clearly exceeded authorized levels. This points to a serious insider threat, raising concerns about contractor negligence and inadequate oversight of third-party access. The investigation is focused on determining precisely how security protocols were bypassed or exploited by the contractor. Questions surrounding the duration of unauthorized access, and the extent of data exfiltration are central to the ongoing investigation.
- Contractor's specific role: The contractor's precise function within the bank's systems will be crucial in understanding the extent of potential damage and the specific vulnerabilities exploited.
- Methods of bypassing security: Investigators will determine whether the breach resulted from weak passwords, social engineering, the exploitation of known software vulnerabilities, or a combination of factors.
- Duration of unauthorized access: The length of time the contractor had unauthorized access is crucial in assessing the extent of the damage and potential data exfiltration.
Analyzing the Vulnerabilities Exposed by the Deutsche Bank Data Center Breach
The Deutsche Bank data center security breach highlights critical vulnerabilities within the bank's security infrastructure. While specifics remain under investigation, potential weaknesses include inadequate access control measures, weak password policies, and a possible lack of multi-factor authentication. The absence of robust monitoring and alerting systems, coupled with potentially infrequent security audits, may have allowed the unauthorized access to persist undetected for an extended period. A thorough vulnerability assessment will be vital in identifying and rectifying all identified weaknesses.
- Lack of robust password policies: Weak or easily guessable passwords are a common entry point for attackers.
- Insufficient access control: The principle of least privilege access—granting only the minimum necessary access rights—should have been implemented rigorously.
- Inadequate monitoring and alerting: Real-time monitoring systems and effective alerts are crucial for detecting unusual activity.
- Absence of regular security audits: Regular audits and penetration testing are essential for identifying and addressing vulnerabilities before they can be exploited.
Lessons Learned and Best Practices for Data Center Security
The Deutsche Bank data center security breach provides invaluable lessons for organizations worldwide. It underscores the urgent need to adopt proactive and comprehensive data center security protocols. Implementing robust access control measures, such as multi-factor authentication and the principle of least privilege access, is paramount. Regular security audits and penetration testing are vital for identifying and mitigating vulnerabilities before they can be exploited. Investing in advanced threat detection systems and developing a comprehensive incident response plan are critical for minimizing the impact of a breach. Finally, robust employee security awareness training is necessary to combat phishing attacks and other social engineering tactics.
- Implementing robust access control measures: Multi-factor authentication, least privilege access, and regular access reviews are crucial.
- Regular security audits and vulnerability assessments: Proactive identification and remediation of vulnerabilities is key.
- Employee security awareness training: Educating employees about security threats and best practices is vital.
- Development of a comprehensive incident response plan: A well-defined plan ensures a swift and effective response to security incidents.
Conclusion: Preventing Future Data Center Security Breaches
The Deutsche Bank data center security breach serves as a stark reminder of the ever-present threat to data center security. The incident emphasizes the need for proactive and comprehensive security measures, extending beyond mere compliance to a culture of continuous improvement and risk management. By implementing the best practices outlined above, organizations can significantly reduce their vulnerability to similar attacks. Strengthening data center security is not just a matter of protecting sensitive data; it's about maintaining operational continuity, safeguarding reputation, and ultimately, ensuring business success. Don't wait for a breach to occur; take proactive steps today to prevent data center breaches and improve data center security protocols within your organization.

Featured Posts
-
 Bayern Muenih Augsburg Maci Canli Izleme Rehberi
May 30, 2025
Bayern Muenih Augsburg Maci Canli Izleme Rehberi
May 30, 2025 -
 Setlist Fm Se Integra Con Ticketmaster Noticias Para Fans De Musica
May 30, 2025
Setlist Fm Se Integra Con Ticketmaster Noticias Para Fans De Musica
May 30, 2025 -
 Six Dismembered Bodies Reconstructing A Serial Killers Death Bath
May 30, 2025
Six Dismembered Bodies Reconstructing A Serial Killers Death Bath
May 30, 2025 -
 Ticketmaster Y Setlist Fm Planifica Tu Proximo Concierto Con Exito
May 30, 2025
Ticketmaster Y Setlist Fm Planifica Tu Proximo Concierto Con Exito
May 30, 2025 -
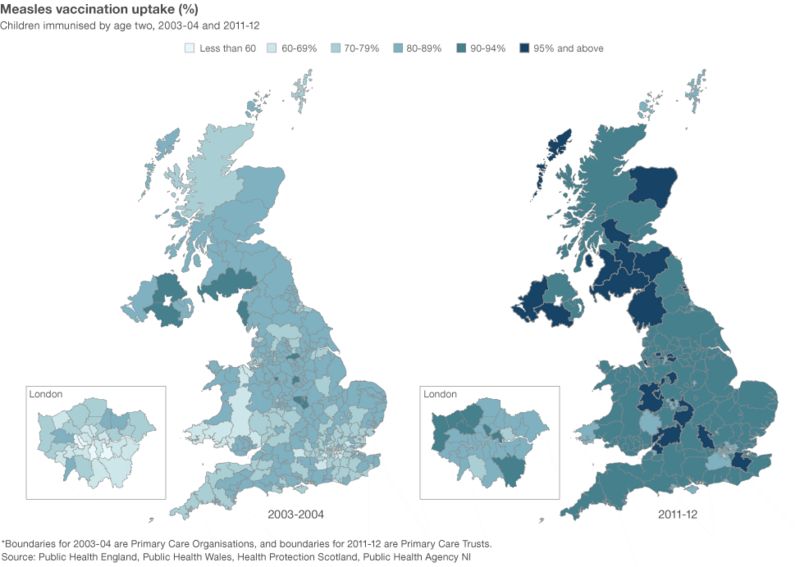 The Slowdown Of Measles Factors Contributing To The Reduced Cases In The Us
May 30, 2025
The Slowdown Of Measles Factors Contributing To The Reduced Cases In The Us
May 30, 2025
