Cybercriminal Made Millions From Compromised Executive Office 365 Accounts
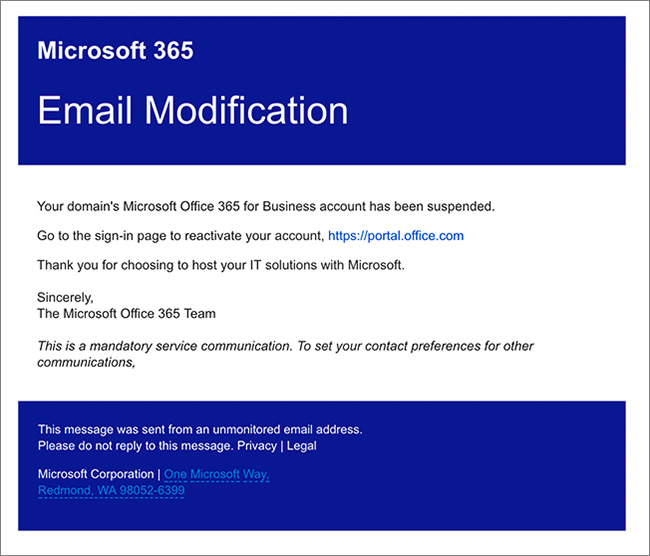
Table of Contents
The Modus Operandi of the Cybercriminal
The cybercriminal employed a multi-pronged attack leveraging advanced phishing and social engineering techniques to gain access to executive Office 365 accounts. Their success highlights the need for continuous vigilance and robust security protocols.
Phishing and Social Engineering Techniques
The attack relied heavily on sophisticated phishing tactics designed to bypass standard email filters and deceive even experienced users.
- Spear Phishing: Highly targeted emails were crafted to mimic legitimate communications from known contacts, such as board members or trusted business partners. These emails often contained links to malicious websites or attachments carrying malware.
- Whaling: This technique targeted high-profile executives directly, employing personalized emails designed to appear legitimate and urgent, often involving requests for immediate financial transfers or sensitive information.
- Social Engineering: The cybercriminal combined these phishing attacks with social engineering, using publicly available information to build rapport with their targets and increase the likelihood of successful deception. They skillfully manipulated employees into revealing credentials through pretexting and other manipulation tactics.
- Exploiting known vulnerabilities: While not detailed in this specific case, the investigation strongly suggests the use of known vulnerabilities in outdated software or plugins to gain a foothold within the network once initial access was granted via phishing.
Exploiting Weak Passwords and Security Gaps
The success of the cybercriminal's campaign was also facilitated by several vulnerabilities within the target organization's security infrastructure.
- Weak Passwords: Many executive accounts used easily guessable passwords or reused passwords across multiple platforms, significantly increasing the risk of compromise.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA allowed the cybercriminal to access accounts even after obtaining usernames and passwords. MFA adds a crucial layer of security, requiring multiple forms of authentication to verify identity.
- Outdated Software and Lack of Security Updates: Outdated software and the absence of regular security updates created vulnerabilities exploited by the cybercriminal to escalate privileges and move laterally within the network.
The Financial Ramifications of the Breach
The financial consequences of this breach of compromised Office 365 accounts were devastating, illustrating the high cost of inadequate cybersecurity.
Scale of the Financial Losses
The cybercriminal successfully siphoned millions of dollars from the company's accounts. The exact figure remains undisclosed due to ongoing investigations, but initial estimates indicate losses exceeding $5 million.
- Methods of Fund Transfer: Funds were primarily transferred via wire transfers and cryptocurrency transactions, making tracing and recovery exceptionally difficult.
- Financial Institutions Involved: Several international banks were implicated in the fraudulent transactions, further highlighting the global reach of this cybercriminal operation.
Reputational Damage and Legal Consequences
Beyond the immediate financial losses, the breach inflicted significant reputational damage on the affected company.
- Loss of Investor Confidence: The news of the breach caused a sharp decline in investor confidence, impacting the company's stock price and overall market valuation.
- Potential Lawsuits and Regulatory Fines: The company faces potential lawsuits from shareholders and regulatory fines for failing to adequately protect sensitive financial information. The incident may also trigger investigations by governmental agencies.
Lessons Learned and Best Practices for Preventing Similar Breaches
This incident serves as a stark reminder of the importance of proactive cybersecurity measures to protect against sophisticated attacks targeting compromised Office 365 accounts.
Strengthening Password Security
Robust password management is fundamental to preventing data breaches.
- Strong, Unique Passwords: Implement a policy requiring strong, unique passwords for all accounts, including executive accounts.
- Password Managers: Encourage the use of reputable password managers to simplify the process of creating and managing complex passwords.
- Regular Password Changes: Enforce regular password changes, ideally every 60-90 days, for all accounts.
Implementing Robust Security Measures
Implementing a multi-layered security approach is crucial to mitigating the risk of compromised Office 365 accounts.
- Multi-Factor Authentication (MFA): Mandate MFA for all accounts, particularly executive accounts, to add an extra layer of security.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities within the network infrastructure.
- Employee Security Awareness Training: Invest in comprehensive security awareness training for all employees to educate them about phishing techniques and social engineering tactics.
- Advanced Threat Protection: Implement advanced threat protection tools, including email security solutions, firewalls, and intrusion detection systems, to detect and prevent malicious activity.
The Importance of Incident Response Planning
Having a well-defined incident response plan is essential for minimizing the impact of a data breach.
- Rapid Response: A quick response is critical to limit the financial losses and reputational damage associated with a breach.
- Clearly Defined Procedures: Establish clear procedures for identifying, containing, and remediating security incidents.
- Regular Testing and Updates: Regularly test and update the incident response plan to ensure its effectiveness in addressing evolving threats.
Conclusion
This case of a cybercriminal making millions from compromised Office 365 accounts underscores the critical need for robust cybersecurity measures. The sophisticated phishing techniques, exploited vulnerabilities, and significant financial losses highlight the devastating consequences of inadequate security practices. By strengthening password security, implementing robust security measures, and developing a comprehensive incident response plan, organizations can significantly reduce their risk of falling victim to similar attacks. Don't become the next victim. Learn more about securing your Office 365 accounts and protecting your business from devastating data breaches today! [Link to relevant security resources]

Featured Posts
-
 Where To Invest A Map Of The Countrys Top Business Locations
Apr 28, 2025
Where To Invest A Map Of The Countrys Top Business Locations
Apr 28, 2025 -
 Shop The Hudsons Bay Liquidation Massive Savings Inside
Apr 28, 2025
Shop The Hudsons Bay Liquidation Massive Savings Inside
Apr 28, 2025 -
 The 2000 Yankees Rally Overcoming The Royals For The Win
Apr 28, 2025
The 2000 Yankees Rally Overcoming The Royals For The Win
Apr 28, 2025 -
 Access To Birth Control The Otc Revolution After Roe V Wade
Apr 28, 2025
Access To Birth Control The Otc Revolution After Roe V Wade
Apr 28, 2025 -
 Solving Americas Truck Bloat Exploring Potential Solutions
Apr 28, 2025
Solving Americas Truck Bloat Exploring Potential Solutions
Apr 28, 2025
Latest Posts
-
 Pirates Walk Off Ends Yankees Extra Inning Fight
Apr 28, 2025
Pirates Walk Off Ends Yankees Extra Inning Fight
Apr 28, 2025 -
 Dramatic Walk Off Pirates Beat Yankees In Extra Innings
Apr 28, 2025
Dramatic Walk Off Pirates Beat Yankees In Extra Innings
Apr 28, 2025 -
 Pirates Walk Off Victory Ends Yankees Extra Innings Battle
Apr 28, 2025
Pirates Walk Off Victory Ends Yankees Extra Innings Battle
Apr 28, 2025 -
 Walk Off Win For Pirates Yankees Fall In Extra Innings
Apr 28, 2025
Walk Off Win For Pirates Yankees Fall In Extra Innings
Apr 28, 2025 -
 Yankees Lose To Pirates On Walk Off Hit After Extra Innings
Apr 28, 2025
Yankees Lose To Pirates On Walk Off Hit After Extra Innings
Apr 28, 2025
