Crook Accused Of Multi-Million Dollar Office365 Executive Email Theft Scheme

Table of Contents
The Alleged Scheme: How the Crook Targeted Executives
This alleged Office365 email theft relied on highly sophisticated techniques, exploiting vulnerabilities in human behavior and system security. The crook allegedly employed spear phishing, a targeted form of phishing, focusing on high-level executives with the authority to approve significant financial transactions. This wasn't a random email blast; this was a meticulously planned attack.
- Spear Phishing Precision: The alleged perpetrator crafted highly personalized emails mimicking legitimate communications from trusted sources, such as board members, clients, or even the CEO. These emails were designed to build trust and bypass suspicion.
- Targeting High-Value Individuals: The targets were carefully selected—high-level executives with access to company funds and the ability to authorize wire transfers. This ensured maximum impact for the minimal effort.
- Gaining Access: The crook allegedly gained access to Office365 accounts through a combination of methods, potentially including exploiting weak passwords, using stolen credentials obtained through other means, or employing social engineering techniques to trick employees into revealing login information.
- Wire Transfer Fraud Execution: Once inside the accounts, the alleged perpetrator used the access to initiate fraudulent wire transfer requests. This often involved sending fake invoices or creating a sense of urgency to pressure the executives into acting quickly without proper verification. The speed and precision of these attacks are a hallmark of sophisticated Business Email Compromise (BEC) schemes.
The Financial Impact: Millions Lost in the Office365 Data Breach
The alleged Office365 data breach resulted in significant financial losses for the victim companies. The exact figures remain undisclosed in many cases, but reports suggest millions of dollars were stolen. The impact extends far beyond the immediate financial loss.
- Quantifying the Losses: While precise figures are often kept confidential, the scale of the losses in this alleged scheme is substantial, potentially impacting the financial stability of affected businesses.
- Reputational Damage: The damage goes beyond mere finances. A data breach, especially one involving executive email compromise, severely damages a company's reputation, eroding trust with investors, clients, and the public.
- Recovery Costs: Beyond the stolen funds, victim companies face significant costs associated with incident response, forensic investigations, legal fees, and the restoration of compromised systems. The long-term impact of these costs can be devastating.
- The Role of Cyber Insurance: While no insurance policy can completely eliminate the pain of a data breach, cyber insurance can significantly mitigate the financial burden. Having a comprehensive policy in place can be crucial for recovery and business continuity.
Lessons Learned: Strengthening Office365 Security Against Email Theft
This alleged Office365 email theft serves as a stark reminder of the vulnerabilities inherent in relying solely on basic security measures. Proactive measures are essential to prevent similar incidents.
- Multi-Factor Authentication (MFA): Implementing MFA for all Office365 accounts is paramount. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access, even if they obtain passwords.
- Advanced Threat Protection: Leverage the advanced threat protection features offered by Office365 and other reputable security solutions. These features can detect and block malicious emails before they reach employees' inboxes.
- Security Awareness Training: Regular security awareness training is not just a good idea; it's a necessity. Employees need to be educated about phishing scams, social engineering tactics, and how to identify suspicious emails. This should include training on identifying sophisticated BEC attacks like the one described.
- Phishing Simulations: Regularly conduct phishing simulations to test employee vulnerability and reinforce training. These simulations help identify weaknesses in your security posture and improve overall awareness.
- Strong Password Policies: Enforce strong password policies and encourage the use of password management tools. Weak passwords are a significant entry point for attackers.
Detecting and Responding to Suspicious Emails
Proactive detection and swift response are critical in mitigating the damage from suspicious emails.
- Identifying Suspicious Emails: Train employees to identify suspicious emails based on indicators like unexpected requests, grammatical errors, unusual sender addresses, or a sense of urgency to act without verification.
- Email Authentication (SPF, DKIM, DMARC): Implement and verify email authentication protocols like SPF, DKIM, and DMARC to authenticate the sender and prevent email spoofing.
- Incident Response Plan: Having a well-defined incident response plan is crucial. This plan should outline clear procedures for handling suspected email breaches, including reporting, investigation, containment, and recovery.
Conclusion
This case of alleged multi-million dollar Office365 executive email theft highlights the significant risks associated with inadequate email security. The sophisticated nature of the scheme underscores the need for proactive measures to protect businesses from similar attacks. The alleged perpetrator's success highlights how easy it is for cybercriminals to exploit vulnerabilities. Don't become the next victim of an Office365 email theft scheme. Implement robust security measures, including multi-factor authentication, advanced threat protection, and regular employee training, to safeguard your organization against these increasingly prevalent cyber threats. Learn more about securing your Office365 environment today!

Featured Posts
-
 The Winning Names Minnesotas Snow Plow Contest Results
Apr 29, 2025
The Winning Names Minnesotas Snow Plow Contest Results
Apr 29, 2025 -
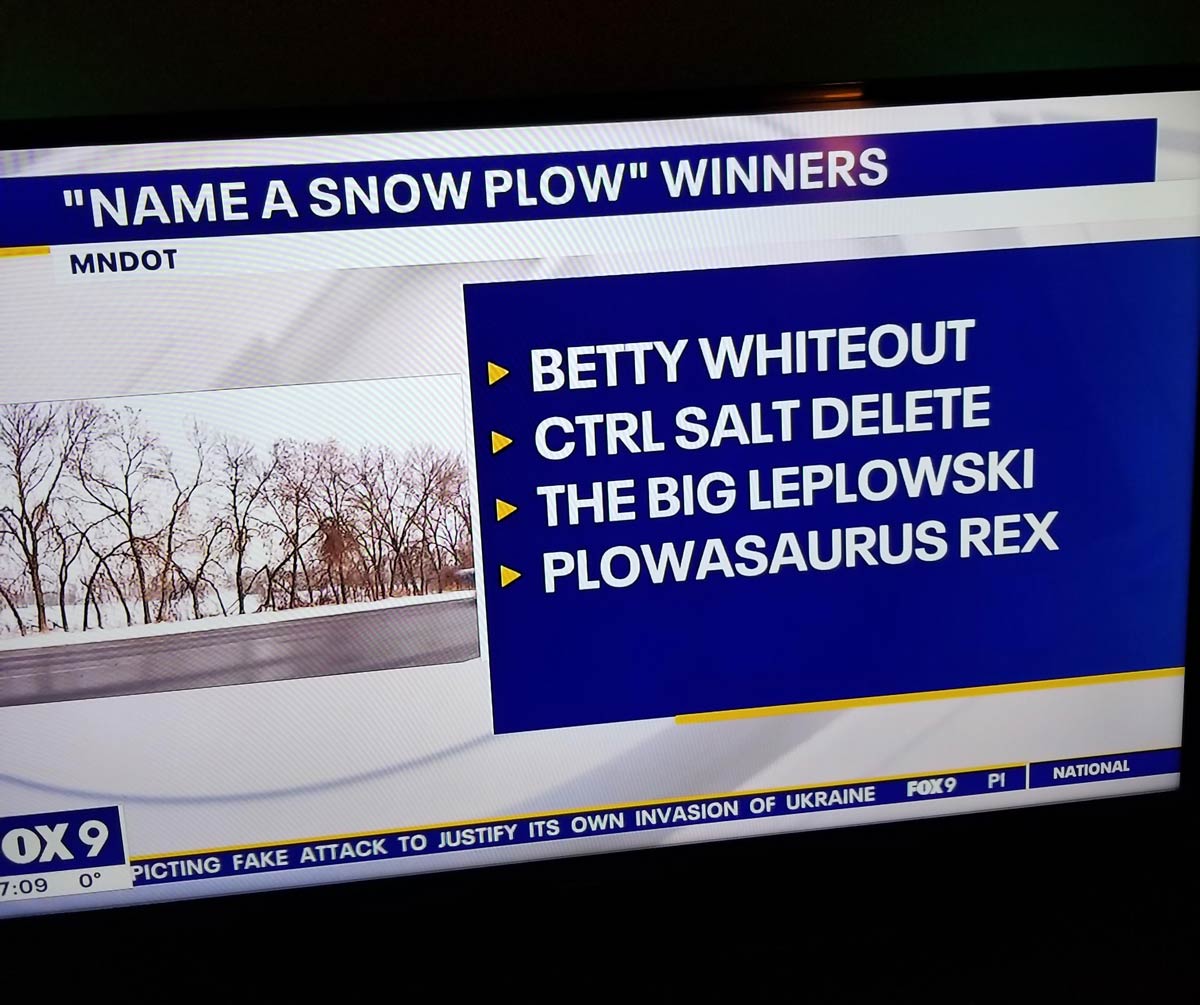 Minnesota Snow Plow Naming Contest Winners Revealed
Apr 29, 2025
Minnesota Snow Plow Naming Contest Winners Revealed
Apr 29, 2025 -
 Hungary Defies Us Pressure Maintaining Strong Economic Ties With China
Apr 29, 2025
Hungary Defies Us Pressure Maintaining Strong Economic Ties With China
Apr 29, 2025 -
 Concerns Rise Over Willie Nelsons Health And Rigorous Tour Life
Apr 29, 2025
Concerns Rise Over Willie Nelsons Health And Rigorous Tour Life
Apr 29, 2025 -
 Ramiro Helmeyer His Pledge To Blaugrana Glory
Apr 29, 2025
Ramiro Helmeyer His Pledge To Blaugrana Glory
Apr 29, 2025
Latest Posts
-
 Donald Trump Calls For Pete Rose Pardon And Hall Of Fame Induction
Apr 29, 2025
Donald Trump Calls For Pete Rose Pardon And Hall Of Fame Induction
Apr 29, 2025 -
 The Pete Rose Pardon Donald Trumps Presidential Gamble
Apr 29, 2025
The Pete Rose Pardon Donald Trumps Presidential Gamble
Apr 29, 2025 -
 Will Trump Pardon Pete Rose The Impact On Baseball And Sports Betting
Apr 29, 2025
Will Trump Pardon Pete Rose The Impact On Baseball And Sports Betting
Apr 29, 2025 -
 Trump Promises Pete Rose A Posthumous Pardon Following Mlb Criticism
Apr 29, 2025
Trump Promises Pete Rose A Posthumous Pardon Following Mlb Criticism
Apr 29, 2025 -
 Trumps Potential Pardon Of Pete Rose A Look At The Mlb Betting Ban
Apr 29, 2025
Trumps Potential Pardon Of Pete Rose A Look At The Mlb Betting Ban
Apr 29, 2025
